Computer Viruses and Malware: Cybersecurity Awareness Month 2022
Categories: Best Practices Cyber Security Awareness Month Security
 Computer viruses and Malware
Computer viruses and Malware
Most people who use computers have heard the terms “malware” and “computer viruses”, but what are they? Malware and computer viruses are usually used synonymously but while it’s true that all viruses are malware, not all malware is a computer virus. Malware, short for malicious software, refers to software that is made to be malicious. Popular types of malware include:
- Phishing: a term used for email messages designed to look legitimate in the hopes of leading you to a fake website or opening a file that may harm your computer, encrypt your data or steal your information. This is one of the most common and frequent forms of malware which makes it especially dangerous. For more information, see https://it.okstate.edu/security-education/phishing.html
- Network sharing: a computer on a network becomes infected and spreads the infection to other computers on the network.
- Trojan: software designed to look identically like other, genuine software that, when activated, allows outside access and control of a device. Some trojans damage the device, either the software or hardware; some trojans steal data.
- Ransomware: software that locks then encrypts data and/or device. Payment is demanded in return for the encryption key to unlock the device/data.
- Adware and Spyware: software designed to push advertising. This software tracks activity through browser cookies and the browser’s history. The software will push pop-up ads and other unwanted advertising. Like other malware, adware/spyware can collect data that would be sold to other parties for identity theft and credit card fraud.
A computer virus is a type of malware that spreads as soon as it is ran on their device. It is attached to another file and spreads as soon as it is opened, either by the user or automatically by the computer. Symptoms of having a virus include:
- Unexpected behavior, such as extreme slowdowns and consistent crashes
- Missing or corrupted files
- Low Storage space on hard drive
- Constant and unexpected browser pop ups
- Unable to run software to check for viruses
- Unidentified programs or apps
Computer viruses can steal your data, send infected files to others on the contact list of the device or on the same network, and even take over other applications.
To keep your technology safe and minimize the risk of malware and computer viruses, use an anti-malware/anti-virus software application. The program acts as a gatekeeper on your computer and monitors and scans activity then notifies and takes action when necessary.
For Windows PCs, the Windows Security app, originally called the Windows Defender, is our go-to application. To access this app on a Windows 10 computer, select the Windows icon on the bottom left of your screen, and then scroll down to Windows Security, as shown in the below photo.
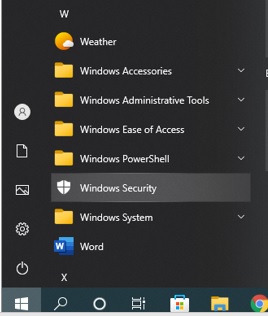
From the Windows Security window, select “Virus & Threat protection” (on the left hand side) then click on “Quick Scan”.
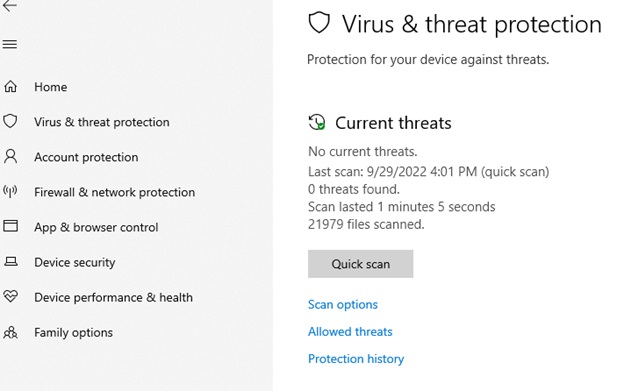
To run the full scan option, click on “Scan Options” as shown above and select the Full Scan option, then click “Scan Now”.
Apple computers has programs for malware protection: Gatekeeper, Xprotect, and MRT (Malware Removal Tool). All three applications should be automatically added and running on your iOS system. Microsoft Defender for Endpoint is also available for Mac at https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-mac?view=o365-worldwide or the App store on your iPhone and Ipad.
Gatekeeper is the security system that checks the integrity and authorization of the software once it is downloaded. It also checks apps running in the background and may not be visible or immediately available.
Xprotect is set to track and block malware from running. You can verify the app is running: click on the Apple logo > About this Mac. Then go to System Report > Software > Installation.
MRT is a three part process that protects the device from malware, with the first layer intended to prevent the downloading of suspicious files, the second layer using XProtect to check apps for malware when they are about to start, and the third removes the malware.
Whether it is a PC, a Mac or a mobile device, the best way to protect your devices comes from prevention:
- Keep your device updated. Updates regularly include security features. It’s suggested that you check for new updates once a week.
- Be aware of suspicious emails. Emails designed to trick users are getting better at looking legitimate. They can imitate personal and corporation accounts and will usually include a hyperlink embedded in the message. When in doubt, use methods of checking that doesn’t include the information on the suspicious email, such as visiting the website in question or contact the person who supposedly sent the email. For more information, check a more in depth description at https://it.okstate.edu/security-education/malicious-emails.html
- Forward suspicious emails and report suspicious technological circumstances to abuse@okstate.edu.
If you receive a suspicious email or your device appears to have a virus or malware, contact your departmental IT Specialist!
Sources:
- https://www.titanfile.com/blog/types-of-computer-malware
- https://hightouchtechnologies.com/9-common-types-of-computer-viruses
- https://us.norton.com/blog/malware/types-of-malware
- https://iboysoft.com/wiki/xprotect-mac.html