Password Safety
Passwords are keys to your online castle(s) such as: employer’s online resources, bank account, social media accounts, shopping sites, health records, and much more. Password safety is not something many people think about on a daily basis but passwords help keep your accounts secure and your digital identity safe. In this article, I explore best practices for password safety.

Password safety begins with strong passwords. You may see many different definitions of a strong password. Over time, we learn better practices to increase the security of a password. These include a password’s length, its uniqueness and randomness, and the feasibility of guessing a password.
Password Length
Let’s start with password length. Many sites require your password to have a minimum number of characters. Why? With each additional character added to the password length, you are exponentially increasing the number of possible combinations needed to crack your password. For someone nefariously trying to crack into your password with a password cracker program, a password with more characters could exceed the ability of the cracker program. The National Institute of Standards and Technology (NIST) recommends at least 8 characters but others suggest at least 12 characters for password length. Eight characters is a reasonably good minimum number of characters for your password but longer passwords are better.
Password: Unique and Random
Another part of a strong password is its uniqueness – not reusing the same password across several websites. This aspect is often overlooked but a unique password is one of the more important factors you should consider. Even the strongest password used over and over on many different websites becomes insecure: if a website is compromised and hackers have login data, your strong but not unique password is now available to the hackers. Once your password is compromised, instead of updating the password for the one site that was hacked, you would need to change the password on every site where you used that password!
Randomness plays an important role in the strength of a password as well. Randomness in your passwords makes them much harder to guess because you use less predictable words or characters. Some may use the names of friends, family, pets, or even the name of the service itself; others use birthdays or some variation of generic passwords like 12345, ‘qwerty’, or just exchanging a letter or two in ‘password’ with a similar symbol like ‘a’ to ‘@’. Let’s be honest: you are not making your password much more secure by using ‘P@ssW0rd’. An example that is less predictable would be something like TeaDriveCubeGlasses a password that I made using the passphrase model below.
Using a Base Password
The likelihood of a guessed password is combated by your password’s uniqueness and randomness. But, what if you use a base password and just change a few characters at the beginning or end of the password? Many websites provide a password strength meter to help determine the strength of a password. However, these meters cannot consider how many times that password has been used, or if your password is similar to another password you’ve used at a site. Using a base password with minor changes should be avoided. As in the previous examples, if your account is compromised on one website, your password and any variation of that password jeopardizes your accounts on other sites.
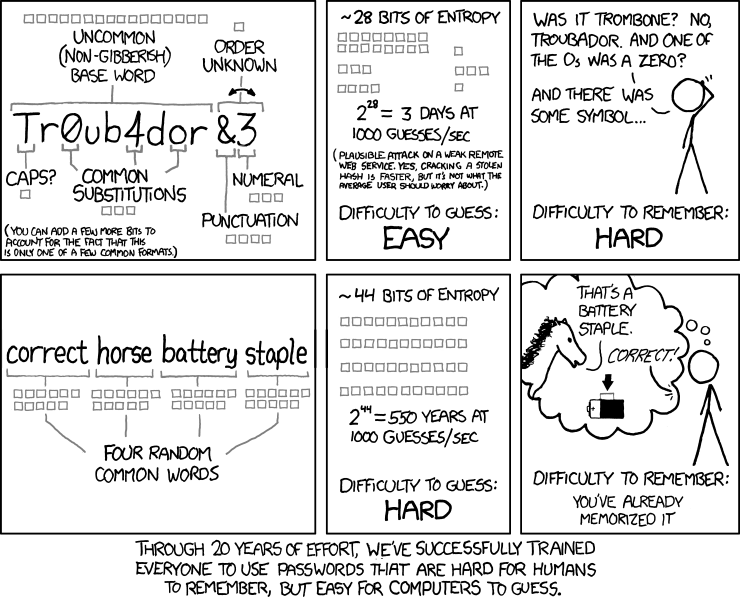
Using a Passphrase
One of the best ways to generate a password is by using a passphrase. A passphrase is a combination of the two words “password” and “phrase”. Using a passphrase as your password (1) helps you create a longer password which is much harder to crack by brute force and (2) allows the password to be more easily remembered. One of the most used examples of a passphrase comes from a comic strip called XKCD. They said the difficulty to remember the passphrase is as: “You’ve already memorized it.”

Password Manager
After you have a strong unique password, you will want a safe and secure way to remember it. Now, some people may have a fantastic memory for remembering hundreds of unique and random passwords, but not everyone is blessed with such a memory. Many people write down their passwords on a piece of paper, maybe an Excel sheet, or even a sticky note under their keyboard. This is another practice that is not very secure. So, you may be wondering how to remember all your long, random, unique passwords! The best course of action is a password manager: a tool that will store all your usernames and passwords for your accounts behind one username and password. This helps keep people without the credentials to your password manager from being able to find your password list and logging into your accounts. There are many different password managers out there including LastPass, Bitwarden, 1Password, and Dashlane to name a few.

Best Practices for Password Safety
Another piece of password safety is knowing when to change your password. Pay attention to news headlines about digital and online security and change your passwords when you become aware of a data breach with of service you use. Change your password – using the techniques described above – to a new, strong password and if you have any other account using the same password, change it too. If you provide an account password to someone, change it as well.
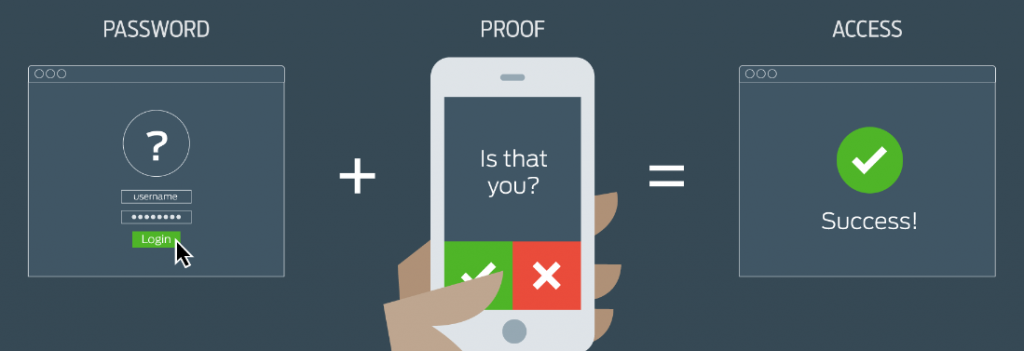
Multifactor authentication (MFA), or two-factor authentication as it is sometimes called, is a security feature that requires two forms of identification to log into an account. There are three different types of identification that can be used for multifactor authentication: something you know, something you have, or something on you. For example, MFA may use a password (something you know), a cell phone (something you have), or a fingerprint (something on you). The two forms of identification need to be different types to help strengthen the security of the account. In our examples, you couldn’t use a password and a pin number as both of those would fall under the “something you know” category but it could a password and a pin number sent as a text message to a mobile phone. Enabling MFA for your account adds another layer of security and helps if your password ever becomes breached: the hacker would need that second factor in order to access your account.
Contact Us
If you have questions related to material covered in this article, about cybersecurity or other IT security related topics, feel free to contact us.
Resource links
https://pages.nist.gov/800-63-3/sp800-63b.html
https://www.loginradius.com/blog/start-with-identity/nist-password-guidelines-2021/
https://www.cloudwards.net/how-to-set-up-a-strong-password/
https://cybernews.com/best-password-managers/how-to-create-a-strong-password/
https://searchsecurity.techtarget.com/definition/multifactor-authentication-MFA
VPN: Not just for work anymore
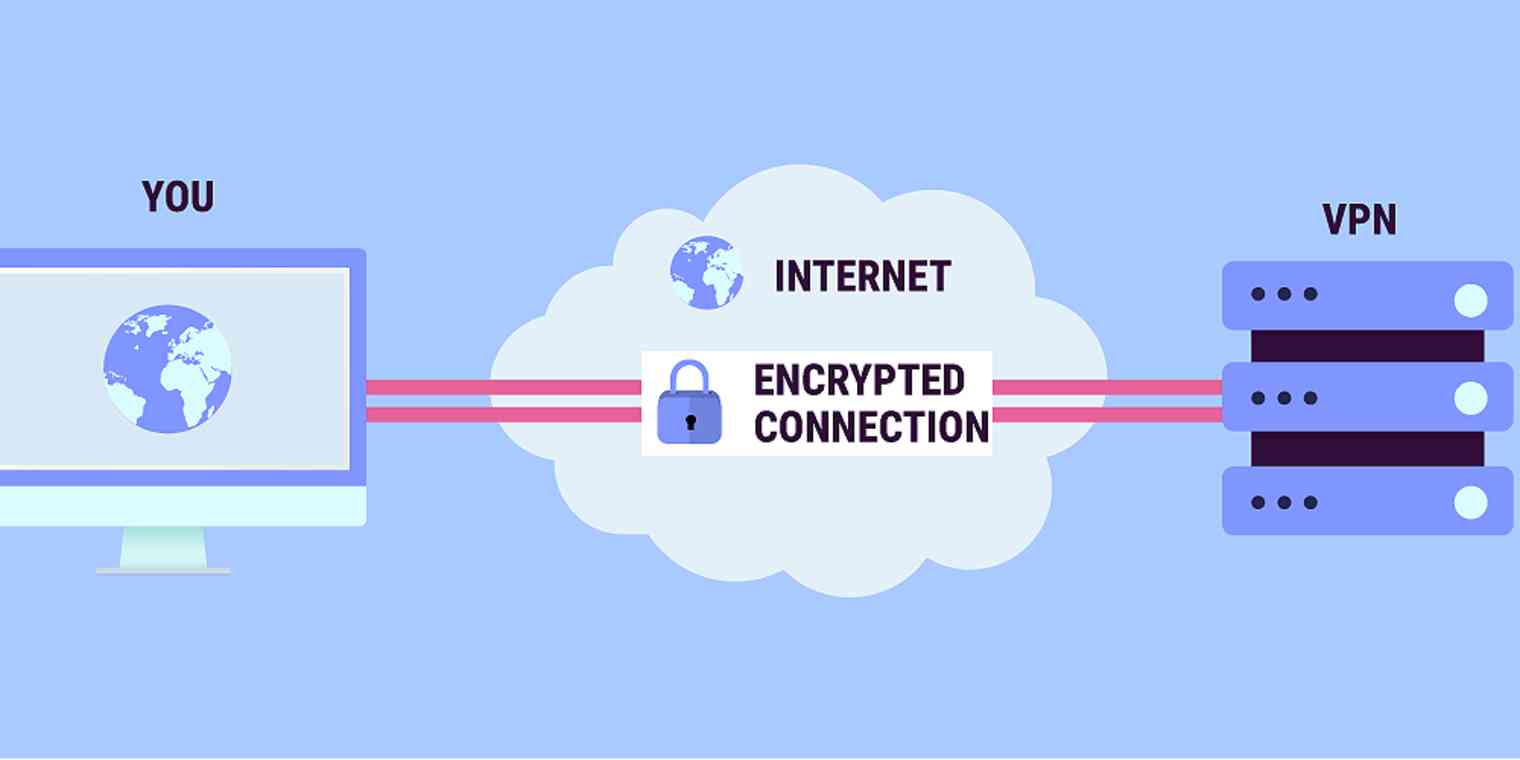
As technology evolves and organizations adapt, our workplace environments have changed so that working remotely – outside the organization’s office space – is now more common and acceptable for both the employer and the employee. When you work from your office at the business’ headquarters, you usually have (hopefully!) IT staff and infrastructure who work to keep your information private and secure. You also may have secured access to on-premise resources such as shared network drives to store documents or a private web portal to access work resources such as SharePoint. But when your office is remote, or mobile, accessing these technologies can be challenging. Using a VPN (Virtual Private Network) becomes a critical link to these resources and is necessary to keep our digital identity and our data safe and secure.
 https://zapier.com/blog/what-is-a-vpn/
https://zapier.com/blog/what-is-a-vpn/
So what is a VPN?
Basically, a VPN is a tool you use on a computer, smart phone, or tablet that helps keep your information secure when your device is connected to a network. It acts as a tunnel between you and your VPN provider to encrypt the information sent over the network. This encryption makes it difficult for people and companies to capture – steal – your information.
How do I get a VPN?
At Oklahoma State University, OSU Information Technology offers a VPN that should be used when your device is outside the campus network and the device is connecting to campus resources or exchanging information with campus resources. You can access this VPN at https://osuvpn.okstate.edu/. This VPN not only encrypts data but it allows your device to access on-campus digital resources. Note that this VPN does not encrypt network traffic (data) between your device and sites outside the okstate.edu domain.

But what about for personal use?
Perhaps you have been using a VPN to connect to work-related resources but what about for personal use at home and when abroad? On your home network the risk of someone snooping and intercepting your data is low but you are still vulnerable as your ISP (Internet Service Provider) can track your activity and, possibly, share the information with other companies. When you visit a coffee shop, airport, or business and they offer WiFi you may be tempted to connect to their wireless network. These networks can have many users and some may be attempting to track your activity, capture information and note your location. A VPN does more than connect you to resources and encrypt your internet traffic: the VPN can hide your location. Especially at these locations, using a VPN is critically important.
There are quite a few companies who offer VPN services and most VPNs must be purchased. I include links, below, to resources and VPN providers. You are encouraged to do research and find out which one works best for you. They offer comparison charts where you can see pricing and features. Take advantage of some of their free trials. To help you decide do some testing by connecting to common websites and evaluating network speeds. If you have questions, feel free to talk to us in DASNR Information Technology.
More Information and Links:
The Best VPN Services for 2021 | PCMag
Best VPN service of 2021 – CNET
VPNs: should you use them? – Malwarebytes Labs | Malwarebytes Labs
⮕ What is a VPN? Virtual Private Network Benefits | NordVPN
https://www.mozilla.org/en-US/products/vpn/
https://www.mozilla.org/en-US/products/vpn/more/what-is-a-vpn/
Don’t Be Held Captive to Ransomware
“$5.9M ransomware attack on major agriculture group poses risk to US grain, pork, chicken supply”
Fox Business
Sept. 21, 2021
What is Ransomware?
Ransomware is a type of malicious attack where attackers encrypt a victim’s data. Ransom is then demanded in exchange for decryption. Hackers often target and threaten to sell or leak sensitive data or authentication information if the ransom is not paid.

Ransomware is big business! In terms of both ransoms paid, spending and lost time in recovering from attacks, an estimated cost to the global economy is approximately $20 billion in 2021, a 57-fold increase from 2015. It’s estimated that 45 percent of ransomware attacks target healthcare organizations while 85 percent of malware infections at healthcare organizations are ransomware.
How ransomware works
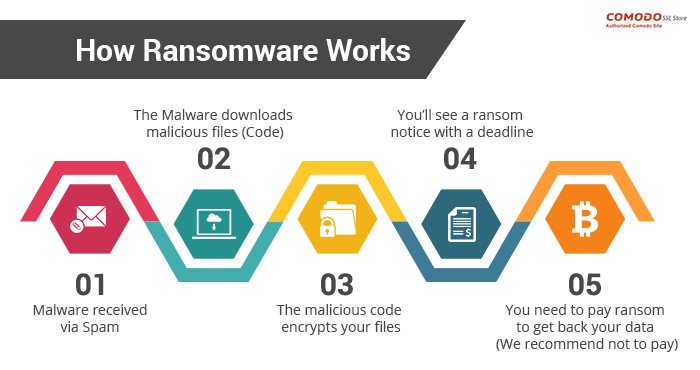
One of the most common delivery mechanisms is phishing email: attachments accompany an email to the potential victim. Once the attachment is downloaded and opened the attack takes over the victim’s computer. Another common delivery mechanism is from malicious websites. An example of how this payload occurs:
- A user is tricked into clicking on a malicious link that downloads a file from an external website.
- The user opens the file, not knowing that the file is ransomware.
- The ransomware takes advantage of vulnerabilities in the user’s computer and uses other computers on the network to propagate throughout the organization.
- The ransomware simultaneously encrypts files on all vulnerable computers then displays messages on their screens demanding payment in exchange for decrypting the files.
At a minimum ransomware disrupts an organization’s operations; a worst case scenario is that ransomware halts an organization’s ability to do business. Ransomware poses a dilemma for an organization’s management: does the organization pay the ransom and hope that the attackers keep their word to restore access, or does the organization not pay the ransom and attempt to restore operations themselves? Payment of ransom does not guarantee a key to unlock the encrypted data and organizations may not be able to completely restore operations after an attack.
Minimizing the risks of a ransomware attack
Fortunately you can take steps to minimize the possibility of a ransomware attack and you can minimize the effects should an attack be successful. Best practices for managing the risk and preventing ransomware attacks include:
- Use strong passwords; use multifactor authentication whenever possible.
- Do not install unauthorized apps! Beware of opening files or clicking on links from unknown sources.
- Be suspicious of unexpected emails.
- Keep your computer updated! Both PC and Mac computers receive updates from Microsoft and Apple. You must enable the installation of these updates.
- Your computers must use antivirus software! Antivirus/antimalware software should automatically scan emails and flash drives. Contact your Computer Support Specialist about installing the enterprise licensed anti-malware software.
- Be prepared: backup your data and regularly test these backups. Create and exercise a basic cyber incident response plan that includes response and notification procedures for a ransomware incident.
- When connecting to a network, choose a secure network and use a virtual private network (VPN) where possible.
Plan for recovery
Steps to follow after ransomware has been detected:
- Determine which systems were impacted and immediately isolate them.
- Only in the event you are unable to disconnect devices from the network, power them down to avoid further spread of the ransomware infection.
- Contact the appropriate authorities.
Steps you can take now to help you plan for recovery from a ransomware attack:
- Develop and test a recovery plan, including an up-to-date list of internal and external contacts for ransomware attacks.
- Carefully plan, implement, and test a data backup and restoration strategy.
Links mentioned or referenced in this article
- https://csrc.nist.gov/projects/ransomware-protection-and-response
- https://www.cisa.gov/stopransomware/ransomware-101
- https://us-cert.cisa.gov/ncas/tips/ST04-003
- https://www.pcgamer.com/windows-10-has-a-built-in-ransomware-block-you-just-need-to-enable-it/
- https://www.cisa.gov/stopransomware
- https://csrc.nist.gov/CSRC/media/Projects/ransomware-protection-and-response/documents/NIST_Ransomware_Tips_and_Tactics_Infographic.pdf
- https://www.cisa.gov/sites/default/files/publications/CISA_MS-ISAC_Ransomware%20Guide_S508C_.pdf
- https://www.cisa.gov/sites/default/files/Ransomware_Trifold_e-version.pdf
Phight the Phish!
Cybersecurity Awareness Week 2: Phight the Phish!
As we head into the second week of Cybersecurity Awareness Month 2021, we should take some time to be aware on how to Phight the Phish! Cyber criminals are coming up with new ways to “phish” for your information using browser redirect hijacks and Windows notifications. “Phishing,” in the tech world, is the fraudulent practice of purporting to be from reputable companies and attempting to induce individuals to reveal personal information, such as passwords and credit card numbers. I’ll show you how to recognize and prevent such things from happening on your end.
What is Browser Hijacking?
We use an internet browser to find and search for content. Common browsers are Chrome, Firefox, Safari and Edge. Browser hijacking occurs when unwanted software is installed on a browser and alters the ability to search for information. This can cause website redirects that open malicious websites where cyber criminals:
- Steal data such as identity, banking and passwords
- Use the video camera and microphone to spy
- Collect keyboard entries
- Display persistent (pop-up) advertising
- Run a try-before-you-buy hard sell advertisement
For example, criminals entice you to visit a website containing scripts that work with your browser to install the malware or you click on a link from this website and malware is installed. Once this happens, your browser has been hijacked!
Should this happen to you, do not call the listed telephone number and do not provide any personal information. Most of these browser hijacking types of attacks are relatively harmless: normally you can reboot your computer or force the browser to close and the issue will go away. We suggest you scan your computer with an anti-malware tool such as Windows Defender to ensure your computer is not infected. If you are unsure of what to do or if you are unsure if something is legit or safe, please contact your Computer Support Specialist.
Another phishing method is to click a link that takes your browser to a website hackers have crafted to mimic a well-known site you often visit. Here, they attempt to capture critical information such as your user ID and account, password, full name, address, social security number, and even answers to security questions — mother’s maiden name, etc. With this information cyber criminals use the information to access your online accounts. This could lead to identity theft and the loss of money.
Why am I getting these ads in my notifications area?
Another popular tool cyber criminals use to phish for your information is a browser notifications plugin. You might be browsing the Internet or working on an Excel spreadsheet and notice a popup in the bottom right part of your screen saying you have viruses or malware. The images below show the difference between an ad and a valid Windows Defender notification.
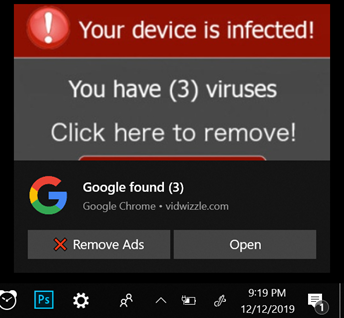 Notification Ad
Notification Ad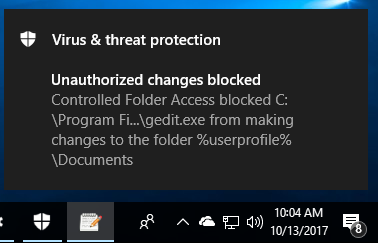 Valid Windows Defender message
Valid Windows Defender messageSimilar to browser redirects, these pop-up notifications are harmless; most of the time they are ads or websites trying to phish for your personal information. You can either ignore these completely or close them out but the easiest thing to do is turn off notifications altogether from whichever browser you use: On a PC, open your Settings window by clicking your start button in the lower left part of your desktop and clicking on the gear icon.
Then click the System option.
Then you will click the Notifications & Actions option in the left menu and you will want to turn OFF the notifications for Chrome or whichever browser you are using. This should disable those ads from reappearing.
While these notification ads are targeted for Windows 10 computers, Mac users might also experience unwanted pop-ups. However, notifications on a Mac are site specific. To prevent sites from showing you intrusive or misleading ads by changing your settings.
- Open Chrome
 .
. - At the top right, click More

 Settings.
Settings. - Under “Privacy and security,” click Site Settings
 Ads.
Ads. - Choose the option you want as your default setting.
#PhightThePhish
We must all do our part in recognizing and adapting to changes in ways online criminals can phish for our personal information. Below are a few links with more tips on how to recognize and be aware on how to PHIGHT THE PHISH!
Be sure to contact your DASNR IT Computer Support Specialist for additional info on phishing attacks!
- https://www.cisa.gov/
- https://www.cisa.gov/cybersecurity-awareness-month
- https://www.cisa.gov/sites/default/files/publications/Cybersecurity%20Awareness%20Month%202021%20-%20Identity%20Theft%20and%20Internet%20Scams%20Tip%20Sheet_0.pdf
- https://www.cisa.gov/sites/default/files/publications/Cybersecurity%20Awareness%20Month%202021%20-%20Phishing%20Tip%20Sheet.pdf
Using Social Media Safely
It is easy to ignore cyber security, to not take proactive steps and to think “That won’t happen to me.” Many people, however, have learned – after their accounts have been breached, data compromised and, even worse, their identity stolen – it is much easier to take steps to protect yourself before something happens than deal with the consequences of simply not caring. October is National Cyber Security Awareness month and it is an excellent opportunity to review our social media activity to consider ways we can improve our security and safety.
Being safe online does not have to be a huge hassle – it really only involves one minor item: Think before you take action. In this article I will dive into this theme and highlight steps you can take to better protect yourself while using social media.
Think before you post!
This is always a good recommendation when using social media! Consider these questions before you submit that post.
- Do I need to post this right now or can it wait? Consider how your post may be giving criminals information about your whereabouts, especially when you will be away for an extended time. While you are on a vacation (or anywhere else that is not home), posting photos, status updates, or, even worse, your location could give thieves enough information to know when to break into your home. A much better choice is to wait and share any photos of your dream vacation when you are safely home.
- Am I giving away any of my personal information? You see it on Facebook: funny and fun quizzes begging you to respond. They usually include something along the lines of “here are my answers copy this and repost with your answers.” These usually don’t ask direct questions like “what is your social security number” they usually ask many indirect questions like “what month were you born in”, “what was your high school mascot”, or “what is your mother’s maiden name?” Consider how you use this information with security questions when setting your passwords. Thieves could get enough information about you to reset a password with information from your answers!
- Do I need to post my child’s game schedule? Similar to #1, above, while it can be a great idea to give your children’s schedule to immediate or close family friends, it is probably something you don’t want to potentially share with the whole world. I realize how proud you may be of your child but the safety of your family is more important. Go to the games, have fun, and take photos – just post them at the appropriate time.
- Do I want this post to be online and associated with my name for the rest of time? Even if you delete a post there is a good chance thata copy of it is digitally saved somewhere. It might have been a friend who thought it was funny and took a screen shot or someone with more sinister plans for using it in the future. If you are not sure, wait 24 hours before you post it – enough time to consider if you really want it on the internet.

Think before you click!
When you are on a roll and having fun while on a computer, it is easy to get ahead of yourself and do something you will regret later. This is another great opportunity to take a few seconds to think before you act.
- Do I know this person and should I add them as a friend? Facebook, Twitter, Instagram and other social media applications can be great tools to reunite or stay up-to-date with friends and family from all over the world. It is also very easy to accept invitations from almost anyone as a friend – even if you do not know them. It is really easy to click that “Accept” button especially when they might already be friends with some of your current contacts. A really good rule of thumb: if you don’t know someone in person, don’t add them on social media.
- Do I really need to click on the link in this post to find out my horoscope, watch a video or play that online game? While it is a very simple to click on a link posted by one of your friends, it can also be dangerous: your computer could get a browser hijack or the link could download malicious software to your computer. When this happens, it is not always as easy as rebooting your computer or uninstalling a program to make a computer problem go away. Ransomware is an example: Clicking the link may result in all the data on your computer becoming encrypted and potentially lost.
Think about security!
Last but probably most importantly, take some time to review the security of your social media security settings. Are your posts visible to just your friends on Social Media or are they viewable by everyone in the world? Is your birthday, anniversary and other important personal information available to everyone or just your friends?

Social media and cyber security
Social media is a great and useful tool but we should use it safely and think about how our actions affects our safety and security. Cyber Security Awareness Month gives us the opportunity to think and to make the needed adjustments to better protect not only ourselves but safely communicate with the people we love.
Links for more information
- https://cybersecurity.ok.gov/content/think-you-click-staying-safe-social-media
- https://www.cisa.gov/sites/default/files/publications/NCSAM_SocialMediaCybersecurity_2020.pdf
- https://home.sophos.com/en-us/security-news/2020/social-media-and-cybersecurity.aspx
- https://blog.hootsuite.com/social-media-security-for-business/
Securing Your Data
This is Cyber Security Month and the topic of many of our articles you’ll read throughout October will outline tools and techniques to protect against malicious programs and users. What are they after – what is their purpose? In addition to a user’s digital identity and the physical network infrastructure, the $150.4 billion a year Cyber Security industry protects a user’s data. In this article, I plan to highlight the need for a data backup plan and provide information about potential plans you can use at work and at home.
The necessity of a data backup plan was part of a conversation that began from a recent email request for tech support:

Hi Mike,
The computer our student workers use for our departmental website, newsletter, etc. is having issues booting up.
Since we are anxious for the newsletter to be released, do you mind
having a look at it at your earliest convenience?
– Thanks
NOTE: When Computer Support Specialists in DASNR IT receive a message stating that a computer is having issues booting up, our thoughts don’t focus just on the computer itself but the data on the computer.
To underscore the need for a data backup:
- How would you replace data on your drive(s) should it become unavailable?
- Do you have data that is, truly, irreplaceable?
Data backup solutions for OSU employees
Now that we have established the need to keep your data safe, what options do we have available at OSU?
According to OSU IT’s website, employees have access to two sources of file storage, OneDrive and network file storage (“Home” drive aka H: Drive). Both options provide storage space that is backed up which allows for data to be restored (within certain parameters) should the need arise.
- OneDrive is a feature of Microsoft® Office 365™, and the network file storage provide drive space for personal documents. Employees get one terabyte (1 TB) of file storage space in OneDrive, as a part of their Office 365 subscription. This is online cloud storage and can be accessed from a multitude of devices: Windows PCs, Macs, via the web, and from a smart phones or tablets devices. To access OneDrive on Windows, open File Explorer and locate OneDrive on the file list located on the left pane. You will need to sign in using your O-Key account. To access OneDrive on Mac, download the OneDrive app from the App Store. Once downloaded, sign into the app to view OneDrive in Finder. To access on a smart phone or tablet download the OneDrive app. Once the app is downloaded, sign in to view your files. For iOS, download from the App Store. For Android, download from the Google Play Store. To access OneDrive via the web, go to cowboymail.okstate.edu, click the App launcher in the top left, and select “OneDrive”. To learn more about OneDrive and its functions, you can check out the blog post created by Bronson Lewis, Extension Support Specialist, DASNR IT, titled “Sync Files with OneDrive in Windows”.
- Employees get 500 MB of personal network drive space, referred to as your “Home Drive.” You can access it from an office computer or, when off campus, through OSU’s Virtual Private Network (VPN). When on campus, the Home Drive can be accessed through File Explorer (Windows) or Finder (Mac). Look for the home drive folder. If you’re not on campus, connect using the OSU VPN. After connecting to the VPN, you will be able to view through File Explorer (Windows) or Finder (Mac). View accessing instructions
Alternative Recommended Solutions
Another solution for backing up your data is a service named iDrive. iDrive has been recommended by Extension Computer Support Specialists for some time now and can offer data backup solutions for users who are not on campus and want to have the security of an online backup. Apart from their competitive pricing, iDrive has many features that help to make it a good, overall backup solution for any type of user, including:
- Continuous Data Protection (CDP) – automatically backs up changes made to files
- Support for Windows, OS X, Android, iOS, and various NAS devices
- Snapshots – restore data to a specific point in time
- IDrive Express – a two-way physical shipment service for faster backups and restores
- Sync – IDrive links all of your devices so whenever a file is updated, it is available on all linked devices
- Share files with anyone
- Ability to back up to local drives
Please note that while iDrive does have a “free” option, most of their support does come with a yearly service fee.

Offline backups
These are great options, but what about those times where you can’t get on the network or internet to access your files? We can follow the example of the client I mentioned earlier – and use an external hard drive. Not all external storage options are created equal. Aside from price, drives vary in speed, portability and storage. Choosing the perfect external drive is best settled by answering one simple question: How does this external drive compare to available network backup solutions (mentioned earlier in this article)? If you need help answering this question or are confused by the options, discuss your situation with a Computer Specialist in DASNR IT or your departmental IT Specialist. More options are available from the links provided below too.
Just do it!
Keeping your data properly archived adds a layer of protection to your sensitive files from malicious activity and it allows for recovery in the event of equipment failure. If you have not initiated a data backup plan, just do it!
Resource URLs
- OSU Online Storage: https://it.okstate.edu/services/online-file-storage-employees/index.html
- PCMag: https://www.pcmag.com/picks/the-best-external-hard-drives
- iDrive: https://www.idrive.com/