Computer Viruses and Malware: Cybersecurity Awareness Month 2022
 Computer viruses and Malware
Computer viruses and Malware
Most people who use computers have heard the terms “malware” and “computer viruses”, but what are they? Malware and computer viruses are usually used synonymously but while it’s true that all viruses are malware, not all malware is a computer virus. Malware, short for malicious software, refers to software that is made to be malicious. Popular types of malware include:
- Phishing: a term used for email messages designed to look legitimate in the hopes of leading you to a fake website or opening a file that may harm your computer, encrypt your data or steal your information. This is one of the most common and frequent forms of malware which makes it especially dangerous. For more information, see https://it.okstate.edu/security-education/phishing.html
- Network sharing: a computer on a network becomes infected and spreads the infection to other computers on the network.
- Trojan: software designed to look identically like other, genuine software that, when activated, allows outside access and control of a device. Some trojans damage the device, either the software or hardware; some trojans steal data.
- Ransomware: software that locks then encrypts data and/or device. Payment is demanded in return for the encryption key to unlock the device/data.
- Adware and Spyware: software designed to push advertising. This software tracks activity through browser cookies and the browser’s history. The software will push pop-up ads and other unwanted advertising. Like other malware, adware/spyware can collect data that would be sold to other parties for identity theft and credit card fraud.
A computer virus is a type of malware that spreads as soon as it is ran on their device. It is attached to another file and spreads as soon as it is opened, either by the user or automatically by the computer. Symptoms of having a virus include:
- Unexpected behavior, such as extreme slowdowns and consistent crashes
- Missing or corrupted files
- Low Storage space on hard drive
- Constant and unexpected browser pop ups
- Unable to run software to check for viruses
- Unidentified programs or apps
Computer viruses can steal your data, send infected files to others on the contact list of the device or on the same network, and even take over other applications.
To keep your technology safe and minimize the risk of malware and computer viruses, use an anti-malware/anti-virus software application. The program acts as a gatekeeper on your computer and monitors and scans activity then notifies and takes action when necessary.
For Windows PCs, the Windows Security app, originally called the Windows Defender, is our go-to application. To access this app on a Windows 10 computer, select the Windows icon on the bottom left of your screen, and then scroll down to Windows Security, as shown in the below photo.
From the Windows Security window, select “Virus & Threat protection” (on the left hand side) then click on “Quick Scan”.
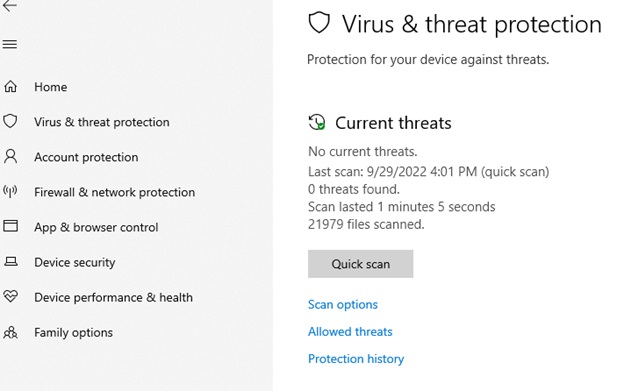
To run the full scan option, click on “Scan Options” as shown above and select the Full Scan option, then click “Scan Now”.
Apple computers has programs for malware protection: Gatekeeper, Xprotect, and MRT (Malware Removal Tool). All three applications should be automatically added and running on your iOS system. Microsoft Defender for Endpoint is also available for Mac at https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-mac?view=o365-worldwide or the App store on your iPhone and Ipad.
Gatekeeper is the security system that checks the integrity and authorization of the software once it is downloaded. It also checks apps running in the background and may not be visible or immediately available.
Xprotect is set to track and block malware from running. You can verify the app is running: click on the Apple logo > About this Mac. Then go to System Report > Software > Installation.
MRT is a three part process that protects the device from malware, with the first layer intended to prevent the downloading of suspicious files, the second layer using XProtect to check apps for malware when they are about to start, and the third removes the malware.
Whether it is a PC, a Mac or a mobile device, the best way to protect your devices comes from prevention:
- Keep your device updated. Updates regularly include security features. It’s suggested that you check for new updates once a week.
- Be aware of suspicious emails. Emails designed to trick users are getting better at looking legitimate. They can imitate personal and corporation accounts and will usually include a hyperlink embedded in the message. When in doubt, use methods of checking that doesn’t include the information on the suspicious email, such as visiting the website in question or contact the person who supposedly sent the email. For more information, check a more in depth description at https://it.okstate.edu/security-education/malicious-emails.html
- Forward suspicious emails and report suspicious technological circumstances to abuse@okstate.edu.
If you receive a suspicious email or your device appears to have a virus or malware, contact your departmental IT Specialist!
Sources:
- https://www.titanfile.com/blog/types-of-computer-malware
- https://hightouchtechnologies.com/9-common-types-of-computer-viruses
- https://us.norton.com/blog/malware/types-of-malware
- https://iboysoft.com/wiki/xprotect-mac.html
Multi-factor Authentication
Multi-factor authentication (MFA) is sometimes referred to as two-factor authentication or 2FA. This is a security feature that requires you to present two types of credentials when logging in. These credentials can be something you know (a password for example), something you have (like a smartphone), or something you are (for example a fingerprint or voice recognition). Multi-factor authentication uses two of the three different types of credentials. As an example, when you log into your email account with your username and password, MFA would require you to enter a code that was sent to your phone. Another common example is after entering your username and password, you have a notification from an authentication app on your phone that asks you if you are trying to log in.
Multi-factor authentication adds an additional layer of security to your account. This makes it much more difficult for someone trying to break into your account. Not only would they need your password but they would also need access to your phone in order to get into the account! Many passwords are compromised every year and MFA helps prevent your accounts from being compromised!
Multi-Factor Authentication is becoming more common. Many websites offer it as a security setting that you would enable to activate. While some may see it as an annoyance or an additional obstacle, MFA adds an additional layer of security and should be considered for any website where you have sensitive information. This includes bank accounts, social media accounts and even shopping websites where you might have saved credit card information.

To verify your identity some websites allow you to set up MFA with a phone number that is used to receive a security code as a text message. This is definitely a positive step and is encouraged but text messages can be intercepted. Consider using an Authenticator app that can be installed on your smartphone and, when used, would generate a code that uses encrypted communication channel. This reduces the potential for compromise. For convenience, some Authenticator apps can be set up to provide a simple notification to either allow or deny a login attempt. Some examples of these kinds of apps are Duo, Authy, Google Authenticator, LastPass Authenticator, and Microsoft Authenticator.
More information can be found here:
- https://www.nist.gov/blogs/cybersecurity-insights/back-basics-whats-multi-factor-authentication-and-why-should-i-care
- https://support.microsoft.com/en-us/topic/what-is-multifactor-authentication-e5e39437-121c-be60-d123-eda06bddf661
- https://www.techradar.com/best/best-authenticator-apps
National Cybersecurity Awareness Month 2022: Personal Awareness
Cybersecurity Awareness Month is a great time to reflect on your habits and how you interact with technology over the past year. With this, answers to the following questions can help you focus on keeping your online identity and your data safe.
 Internet Security
Internet SecurityHave you connected to any public Wi-Fi networks over the last year?
While it is convenient to connect to public networks when at a conference, hotel, restaurant, or coffee shop, it can also be dangerous. If you must connect to the network, avoid doing any banking, online shopping or other online activity you would not like to keep private. Public networks could have users watching, tracking and collecting your activity such as login and banking information.
Have you used any public computers over the last year?
Similar to public Wi-Fi networks, there are risks using publicly-accessible computers. If you log into any secured sites from these computers, your login information could be at risk. For example any site you visit could be listed in the internet browser’s history. If you must use a publicly available computer, ensure that you log out of any sites you previously logged into and when asked, do not store information on the computer. Limit your use on these computers as much as possible.
Have you allowed anyone to use your computer without you being present?
One of the most important parts of security when it comes to technology is acting as a gatekeeper for your technology. People you do not know or do not trust should not have access to your computer or other personal computing devices. If someone is looking to do something nefarious to you, access to your computer will allow them to accomplish their goals. (This is also why it is very important to have a password on your computer.) Even allowing known guests to access your computer could put your system at risk since they could accidentally access sites that install malware on your computer or make online purchases from secure sites where you have stored credit card information.
When was the last time that you purposely updated your computer?
One of the easiest things you can do to help keep your computer, your online identity and your data secure is to simply keep your computer up to date. This doesn’t have to be a huge event where you spend hours a week to ensure that all updates are installed. You simply need to check your computer updates once or twice a month and make sure that they are being installed. Normally Microsoft Windows will install updates without your intervention. However, it will need to be rebooted occasionally and it is a very good idea to check to be sure your updates are being installed. Windows updates can be easily accessed through the setting menu.
Are you talking with your children and other loved ones about computer security?
One thing that can be easily overlooked is ensuring your family knows about computer security. Even when technology is taught in schools, there are some things overlooked or simply not taught. You don’t need to make this a huge deal with your family, but technology and online safety should be considered. If you want to make it a little more fun for younger family members, look online for resources like this video.
Cybersecurity doesn’t need to feel like a huge hassle. Taking a few small steps can make all the difference when it comes to keeping you, your online identity and your data safe.
For additional information on this topic please see the following sites.
1. https://consumer.ftc.gov/articles/how-safely-use-public-wi-fi-networks
2. https://www.nortonlifelockpartner.com/security-center/safety-tips-using-public-computer.html
3. https://privacy.thewaltdisneycompany.com/en/internet-safety/