Don’t Be Held Captive to Ransomware
Categories: Best Practices Cyber Security Awareness Month Security
“$5.9M ransomware attack on major agriculture group poses risk to US grain, pork, chicken supply”
Fox Business
Sept. 21, 2021
What is Ransomware?
Ransomware is a type of malicious attack where attackers encrypt a victim’s data. Ransom is then demanded in exchange for decryption. Hackers often target and threaten to sell or leak sensitive data or authentication information if the ransom is not paid.

Ransomware is big business! In terms of both ransoms paid, spending and lost time in recovering from attacks, an estimated cost to the global economy is approximately $20 billion in 2021, a 57-fold increase from 2015. It’s estimated that 45 percent of ransomware attacks target healthcare organizations while 85 percent of malware infections at healthcare organizations are ransomware.
How ransomware works
One of the most common delivery mechanisms is phishing email: attachments accompany an email to the potential victim. Once the attachment is downloaded and opened the attack takes over the victim’s computer. Another common delivery mechanism is from malicious websites. An example of how this payload occurs:
- A user is tricked into clicking on a malicious link that downloads a file from an external website.
- The user opens the file, not knowing that the file is ransomware.
- The ransomware takes advantage of vulnerabilities in the user’s computer and uses other computers on the network to propagate throughout the organization.
- The ransomware simultaneously encrypts files on all vulnerable computers then displays messages on their screens demanding payment in exchange for decrypting the files.
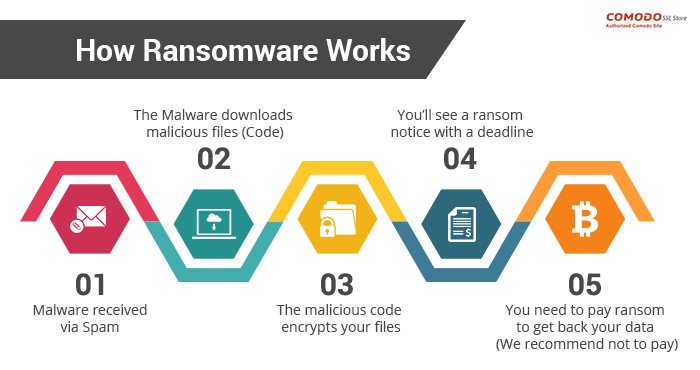
At a minimum ransomware disrupts an organization’s operations; a worst case scenario is that ransomware halts an organization’s ability to do business. Ransomware poses a dilemma for an organization’s management: does the organization pay the ransom and hope that the attackers keep their word to restore access, or does the organization not pay the ransom and attempt to restore operations themselves? Payment of ransom does not guarantee a key to unlock the encrypted data and organizations may not be able to completely restore operations after an attack.
Minimizing the risks of a ransomware attack
Fortunately you can take steps to minimize the possibility of a ransomware attack and you can minimize the effects should an attack be successful. Best practices for managing the risk and preventing ransomware attacks include:
- Use strong passwords; use multifactor authentication whenever possible.
- Do not install unauthorized apps! Beware of opening files or clicking on links from unknown sources.
- Be suspicious of unexpected emails.
- Keep your computer updated! Both PC and Mac computers receive updates from Microsoft and Apple. You must enable the installation of these updates.
- Your computers must use antivirus software! Antivirus/antimalware software should automatically scan emails and flash drives. Contact your Computer Support Specialist about installing the enterprise licensed anti-malware software.
- Be prepared: backup your data and regularly test these backups. Create and exercise a basic cyber incident response plan that includes response and notification procedures for a ransomware incident.
- When connecting to a network, choose a secure network and use a virtual private network (VPN) where possible.
Plan for recovery
Steps to follow after ransomware has been detected:
- Determine which systems were impacted and immediately isolate them.
- Only in the event you are unable to disconnect devices from the network, power them down to avoid further spread of the ransomware infection.
- Contact the appropriate authorities.
Steps you can take now to help you plan for recovery from a ransomware attack:
- Develop and test a recovery plan, including an up-to-date list of internal and external contacts for ransomware attacks.
- Carefully plan, implement, and test a data backup and restoration strategy.
Links mentioned or referenced in this article
- https://csrc.nist.gov/projects/ransomware-protection-and-response
- https://www.cisa.gov/stopransomware/ransomware-101
- https://us-cert.cisa.gov/ncas/tips/ST04-003
- https://www.pcgamer.com/windows-10-has-a-built-in-ransomware-block-you-just-need-to-enable-it/
- https://www.cisa.gov/stopransomware
- https://csrc.nist.gov/CSRC/media/Projects/ransomware-protection-and-response/documents/NIST_Ransomware_Tips_and_Tactics_Infographic.pdf
- https://www.cisa.gov/sites/default/files/publications/CISA_MS-ISAC_Ransomware%20Guide_S508C_.pdf
- https://www.cisa.gov/sites/default/files/Ransomware_Trifold_e-version.pdf