VPN: Not just for work anymore
As technology evolves and organizations adapt, our workplace environments have changed so that working remotely – outside the organization’s office space – is now more common and acceptable for both the employer and the employee. When you work from your office at the business’ headquarters, you usually have (hopefully!) IT staff and infrastructure who work to keep your information private and secure. You also may have secured access to on-premise resources such as shared network drives to store documents or a private web portal to access work resources such as SharePoint. But when your office is remote, or mobile, accessing these technologies can be challenging. Using a VPN (Virtual Private Network) becomes a critical link to these resources and is necessary to keep our digital identity and our data safe and secure.
 https://zapier.com/blog/what-is-a-vpn/
https://zapier.com/blog/what-is-a-vpn/
So what is a VPN?
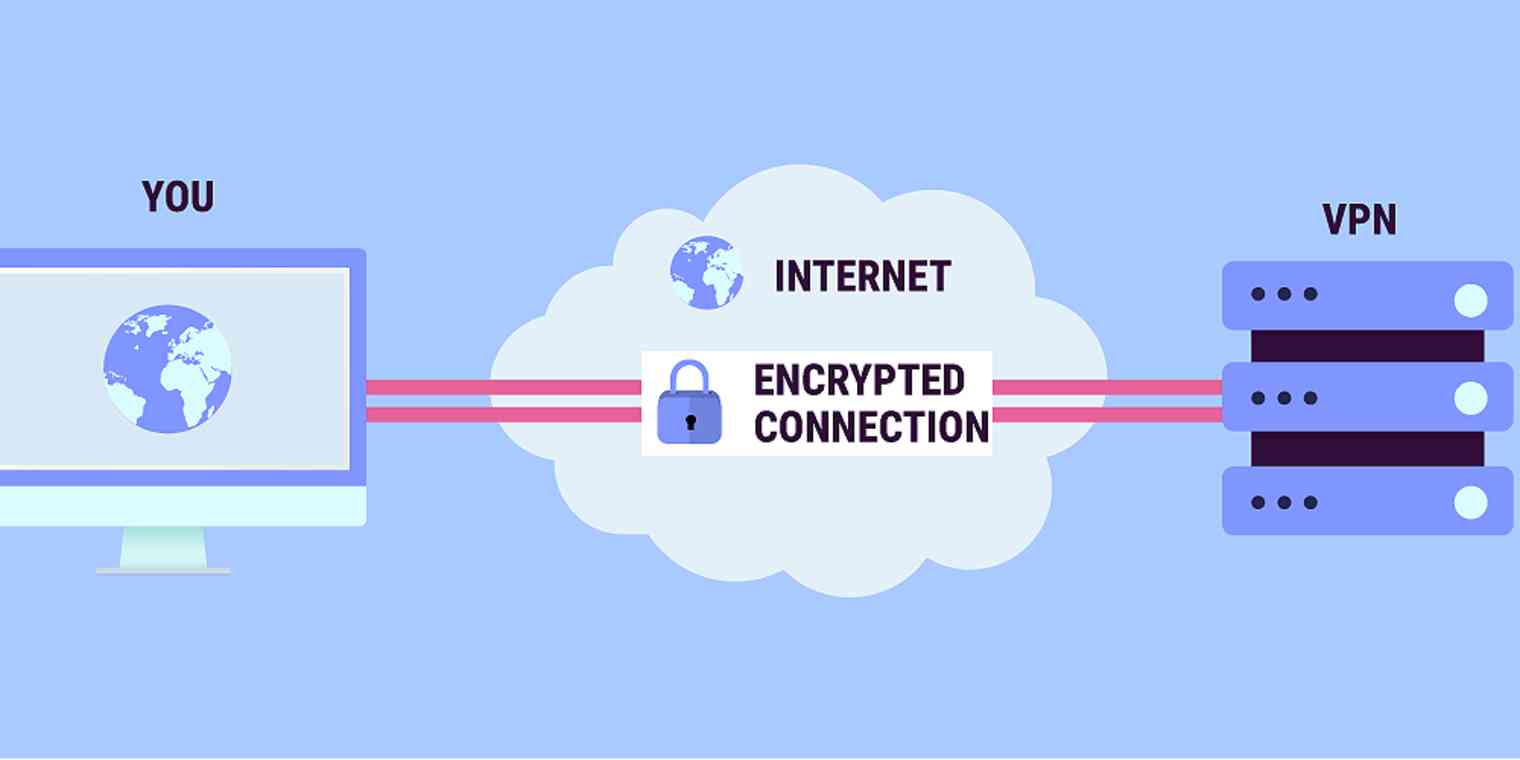
Basically, a VPN is a tool you use on a computer, smart phone, or tablet that helps keep your information secure when your device is connected to a network. It acts as a tunnel between you and your VPN provider to encrypt the information sent over the network. This encryption makes it difficult for people and companies to capture – steal – your information.
How do I get a VPN?
At Oklahoma State University, OSU Information Technology offers a VPN that should be used when your device is outside the campus network and the device is connecting to campus resources or exchanging information with campus resources. You can access this VPN at https://osuvpn.okstate.edu/. This VPN not only encrypts data but it allows your device to access on-campus digital resources. Note that this VPN does not encrypt network traffic (data) between your device and sites outside the okstate.edu domain.

But what about for personal use?
Perhaps you have been using a VPN to connect to work-related resources but what about for personal use at home and when abroad? On your home network the risk of someone snooping and intercepting your data is low but you are still vulnerable as your ISP (Internet Service Provider) can track your activity and, possibly, share the information with other companies. When you visit a coffee shop, airport, or business and they offer WiFi you may be tempted to connect to their wireless network. These networks can have many users and some may be attempting to track your activity, capture information and note your location. A VPN does more than connect you to resources and encrypt your internet traffic: the VPN can hide your location. Especially at these locations, using a VPN is critically important.
There are quite a few companies who offer VPN services and most VPNs must be purchased. I include links, below, to resources and VPN providers. You are encouraged to do research and find out which one works best for you. They offer comparison charts where you can see pricing and features. Take advantage of some of their free trials. To help you decide do some testing by connecting to common websites and evaluating network speeds. If you have questions, feel free to talk to us in DASNR Information Technology.
More Information and Links:
The Best VPN Services for 2021 | PCMag
Best VPN service of 2021 – CNET
VPNs: should you use them? – Malwarebytes Labs | Malwarebytes Labs
⮕ What is a VPN? Virtual Private Network Benefits | NordVPN
https://www.mozilla.org/en-US/products/vpn/
https://www.mozilla.org/en-US/products/vpn/more/what-is-a-vpn/
End of Life (EOL) Are You Safe?
We all know about our software always wanting to install updates. Windows, Office, Adobe, Zoom, and just about any other software we install. At some point your software wants you to install, buy, download, or do an upgrade to a new version. This usually means the previous software versions will no longer be supported, End of Life (EOL). Now, this doesn’t mean the software will no longer work but it means it will no longer be supported.
Why should we be concerned about a software application that will be EOL? When software becomes unsupported there are a few things that change:
- No more security updates to prevent hacks
- The loss of protection against potential viruses
- The software may not work with our new device or computer
- No more bug fixes
- No more performance and reliability updates
Earlier this year many of us had to upgrade to Windows 10 because Windows 7 was EOL on January 14th, 2020. If we did not upgrade, our machine would be open to malicious attacks because Microsoft stopped providing security updates. With the release of Windows 10 Microsoft changed the way they do version upgrades. Versions of Windows now look more like something like this: Windows 10, version 1909. These version releases are aimed to being released twice a year. Their projected months of release are March and September. The version number is coded with the first two digits are the year and the second two are the month of when it was released 1909 = Year was 2019 and Month was September. These versions also become EOL and will eventually need to be upgraded. You can find out more about Microsoft’s EOL versions here: https://support.microsoft.com/en-us/help/13853/windows-lifecycle-fact-sheet
The Windows operating system isn’t the only software that needs to be updated. Microsoft Office is also affected by EOL. You may be running an old version which is missing important patches, fixes and features. Another consideration when looking at EOL of products is Mainstream Support vs. Extended Support. Mainly the difference between the two is Mainstream Support provides feature updates, security updates, and bug fixes. The next layer of support could be Extended Support which usually means you will only get security updates. Microsoft has made an easy way to look up EOL on their products via the search bar on this page: https://support.microsoft.com/en-us/lifecycle/search If you look at this page and search for Office 2016 you will see Mainstream Support ends on 10/13/2020 but Extended Support does not end until 10/14/2025.
So, how can I find information about software I use other than from Microsoft? The best way is to visit the software site and find your version. This may tell you when your EOL date is for that version. Another way is to type in a web search for the product you have and using “EOL” or “End of Life” as part of the search. Just make sure the links you click for the product link to the manufacture’s page. For example, I searched for Adobe EOL and it suggested I visit this page: https://helpx.adobe.com/support/programs/eol-matrix.html Here I found a full list of Adobe products with their Versions, Release Dates, and End of Support dates.
Computing hardware (computers) can also have EOL dates. We update drivers on our computers, phones and tablets as well. Hardware can also have vulnerabilities that lead to security risks, bugs and compatibility issues. With hardware the thing to worry about the most is compatibility. You may have an old computer that you can’t update to a new version of Windows, or it may upgrade to Windows 10, but you cannot get Adobe to work because your video card isn’t supported. Hardware should not be overlooked when thinking about upgrades.
So now what? Well, maybe it’s time to do some inventory. This means both software and hardware. Take note of what software versions and hardware you have and look them up online. Find those EOL dates and see if you need to upgrade or replace something. You don’t have to do this often since a lot of companies will usually give you EOL dates far in advanced so you can prepare. Try and do this about once a year and you should have plenty of time to get everything up to date.
-Mike Rasmussen
Reference Articles and EOL Links:
https://apps.okstate.edu/itannounce/index.php/module/FullStory/action/FullStory?id=16348&From=Home
https://www.spiceworks.com/it-articles/end-of-life-software-dangers/
https://en.wikipedia.org/wiki/End-of-life_(product)
https://helpx.adobe.com/support/programs/eol-matrix.html
https://support.microsoft.com/en-us/lifecycle/search/1163
https://support.microsoft.com/en-us/help/13853/windows-lifecycle-fact-sheet
https://docs.microsoft.com/en-us/lifecycle/faq/general-lifecycle
Updates and Upgrades: Do It!
Almost every electronic device we own these days keeps bugging us to do updates or upgrades – our computers, phones, TV’s, cars and most everything else. We receive notifications asking us to install updates, sometimes weekly, and it always seems at the most inconvenient times. But, updates and upgrades play a critical roll in keeping you and your devices safe.
Updates vs. Upgrades, what is the
difference?
An update will modify your
current software with security patches, small improvements, and bug fixes.
These are what we generally see on a daily, weekly, and monthly basis. They
generally don’t take as long to download and install.
An upgrade will make significant changes to the software that operates on your device. This could be the device’s interface – how it looks and its options. Upgrades are not as common as updates and will usually only happen once or twice a year. They are usually larger in size and can take a long time to install.
When should I install these updates and upgrades?
The simple answer for updates: ASAP. I mentioned earlier that these seem to happen at the most inconvenient times. You don’t have to stop what you are doing but you should install updates at a convenient time after you receive notification they are available. Usually I install them right before I go to lunch or at the end of the day. This way I can reboot my computer or device while I am out and it will be ready when I return. In most cases software updates will only take a few minutes, but I have seen them take 30+ minutes. This can happen if you have gone a while without updating your device, your device is old and slowing down, or possibly a large patch to your software is available.
Upgrades usually do not need to be installed ASAP. Software manufacturers usually allow a certain amount of time before they force you to upgrade. They will continue to provide updates for their older version until they feel they cannot support it any longer at which point you, then, must upgrade your software to a newer version so you can receive necessary security updates. Before you do an upgrade you should check to see if your other hardware or software is compatible with an upgrade. Software and hardware manufacturers will usually list compatible and incompatible devices and versions on their website.
What if I cannot
upgrade?
There are times when doing an upgrade is not something you are able to do. Maybe the equipment you have attached to your computer will not work with an upgrade. You may not have the money to spend on upgrading software and hardware. You should always consider future upgrades as part of a long-term plan when budgeting but that does not always happen. In these cases, you will want to ask yourself a few basic questions: Do I need this connected to the internet or will I be connecting external devices to this equipment? If you answered yes to either of these you need to find a way to upgrade your equipment.
By removing your device from the internet it makes it less vulnerable from any type of hack or security exploit. This will prevent direct attacks on your device since there will be no connection to the outside world. They could still have indirect access to your device if you happen to connect an external device to the machine. USB flash drives, external hard drives, and other media can become infected and then, when attached to your device, they infect your device. They may not gain remote access to your computer or files, but they could spread a virus or Crypto lock on your files. This could lead to a loss of some or all of your data.
So why is this a
significant topic right now?
Well, to be honest, this is a topic that should always be significant. The reason we want to bring it up again now is that Microsoft will be making Windows 7 End of Life (EOL) on January 14th, 2020. This means that Microsoft will not be releasing any more security updates, improvements, or bug fixes. When products go End of Life, it becomes a prime time for hackers to release their exploits to these machines since they know that the software will not be patched any longer and they release any hidden exploits. Keeping up with updates and upgrades are a critical role to make sure you and your devices stay safe.
Information about Windows 7 End of Life: https://www.microsoft.com/en-us/microsoft-365/windows/end-of-windows-7-support
Recovery After A Data Breach – Cyber Security Awareness Month 2017
You have done everything you are supposed to: You don’t use the same password more than once, you don’t click on the fake links in your email or on websites, you use two-factor authentication when you log into websites[1] and you have credit monitoring on your accounts. Then you learn a company you rely on to keep your data private has been hacked. The company has suffered a massive data breach and hackers have your private information. Now what?
First, be aware scammers may have obtained your email address and sent you a falsified email message. After a major data breach, such as the recent one with Equifax[2], hackers often send emails to people trying to get anxious individuals to click on provided links to phishing websites, sites that may look legitimate but ask people to enter private information the cyber criminals then steal. Instead of clicking on links in these types of messages, look up the stated company online and go directly to the website identified by the search engine rather than clicking the link in the possibly falsified original email; better yet, contact the company by telephone and check things out verbally first. In the case of Equifax, the company added a web link and additional information on their page enabling people to check and see if they were affected.
Second, understand your options. The Federal Trade Commission has set up a site that provides additional information[3]: https://identitytheft.gov/. This site can help put together a plan of action both before and after your information has been used by hackers[4]. The FTC offers preventative measures like freezing your credit and signing up for credit monitoring. They also include a list of sites you can visit to see if your information was leaked.
As we become more and more digitally connected, we know these types of issues will continue to happen. Being prepared and having a plan when – and it is when and not if – a data breach happens will allow you to minimize further damage.
[1] http://spotlight.okstate.edu/dasnrit/2017/10/04/passwords-cyber-security-awareness-month-2017/
[2] https://www.consumer.ftc.gov/blog/2017/09/equifax-data-breach-what-do
[3] https://identitytheft.gov/Assistant
[4] https://www.identitytheft.gov/Info-Lost-or-Stolen
Windows 10 now has ads in File Explorer, and this is how to remove them.
Recently Microsoft has decided to start embedding ads into File Explorer. Not Internet Explorer, but File Explorer. When you open up a folder like My Documents or My Computer you can now have an ad placed at the top of the window. I have seen this recently myself and the internet is buzzing about it. Unfortunately it is automatically enabled by default, but luckily you can disable it.
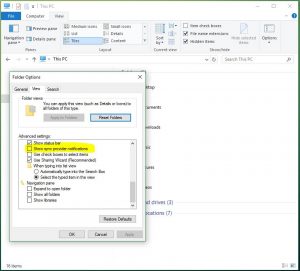
- Launch File Explorer
- Click the View Tab and select Options
- Under Folder Options, click the View tab
- In the Advanced Settings window scroll down to the bottom.
- Somewhere close to the bottom you should see “Show sync provider notifications”. You will want to uncheck this box.
- Click Apply then OK.
So far this should disable ads from inside File Explorer. This is very new and only been happening for a few days. It seems to run ads for products you may already be using, but they offer a “Pro” version at a cost. Just be careful of these, because there has not been a lot of detail about what the ads may contain. It could possibly make it where you think you may need to update your software when you do not need to.
-Mike Rasmussen
Cybersecurity Awareness Month 2016: Passwords and Why Not to Use the Same One
We have been told to never use “easy” passwords and we should not use the same password for all our separate accounts. Well, why is all this fuss necessary? If the site is secure then what is the issue?
One problem is that most of the time hackers are not specifically targeting you or your account. They are focusing their hacking attempts on large companies with millions of usernames and passwords. Companies hacked and the number of accounts exposed in 2015:
- VTech (a toy tech company aimed for kids) 4.8 million
- T-Mobile – 15 million – names, addresses, SS#, passport numbers
- Scottrade – 4.6 Million – didn’t release info about it until 2 years later
- BlueCrossBS – 10 million – found out they had been hacked over a 2 year period
- CVS/Walgreens – Unknown Millions – Credit Cards, email, passwords, addresses
- LastPass (password manager) – data breach – passwords will need to be decrypted
- And most recently Yahoo revealed it was hacked in 2014 and the data breach affects 500 million users. They didn’t let anyone know about the breach until late September 2016.
Now, say they have hacked one of the companies above and you have an online account with one of these companies. More than likely you use the same username or email address to all or most of the other sites that require some form of authentication. In this case these hackers now have at least half of your security breached. With this stolen data, they can run automated programs to decrypt passwords. “Easy” passwords – those that do not contain both upper and lowercase letters, numbers, and special characters – are less challenging to crack and decrypt. For each of the decrypted passwords, the hackers have the full combination of username and password for your account. They assume most people will use the same username/password combination on other sites. So the hackers can attempt to use this newfound information on other sites, or they can sell the information to other hackers who will compromise your other online accounts, such as banking, shopping, bill paying, and personal/family insurance sites.
In some cases, companies don’t know they have been breached – sometimes for years. BlueCrossBlueShield didn’t discover their security breach for almost 2 years. Some companies will immediately disclose the data compromises but others may withhold the information for fear the news will negatively affect their business. When the news is not shared with account holders, the hackers have time to take the information and continue compromising accounts on other systems before users are made aware of the security breach. Identity theft is an unfortunate outcome of these circumstances. Imagine your headaches when all of your accounts are hacked at the same time!
Here are some tips on making a secure password that is easy to remember, but difficult to crack: 6 Tips For Creating An Unbreakable Password.
It is a good habit to use different passwords on your online accounts and frequently change the passwords. We all understand the inconvenience to have multiple passwords, but so is removing a fraudulent charge on your credit card or trying to recover from identity theft.
Mike Rasmussen
Computer Support Specialist, DASNR