Securing Your Data
This is Cyber Security Month and the topic of many of our articles you’ll read throughout October will outline tools and techniques to protect against malicious programs and users. What are they after – what is their purpose? In addition to a user’s digital identity and the physical network infrastructure, the $150.4 billion a year Cyber Security industry protects a user’s data. In this article, I plan to highlight the need for a data backup plan and provide information about potential plans you can use at work and at home.
The necessity of a data backup plan was part of a conversation that began from a recent email request for tech support:

Hi Mike,
The computer our student workers use for our departmental website, newsletter, etc. is having issues booting up.
Since we are anxious for the newsletter to be released, do you mind
having a look at it at your earliest convenience?
– Thanks
NOTE: When Computer Support Specialists in DASNR IT receive a message stating that a computer is having issues booting up, our thoughts don’t focus just on the computer itself but the data on the computer.
To underscore the need for a data backup:
- How would you replace data on your drive(s) should it become unavailable?
- Do you have data that is, truly, irreplaceable?
Data backup solutions for OSU employees
Now that we have established the need to keep your data safe, what options do we have available at OSU?
According to OSU IT’s website, employees have access to two sources of file storage, OneDrive and network file storage (“Home” drive aka H: Drive). Both options provide storage space that is backed up which allows for data to be restored (within certain parameters) should the need arise.
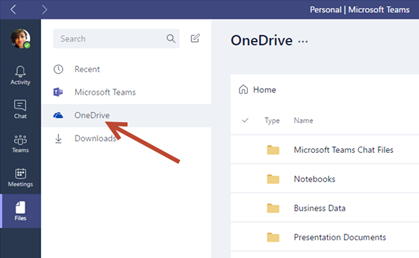
- OneDrive is a feature of Microsoft® Office 365™, and the network file storage provide drive space for personal documents. Employees get one terabyte (1 TB) of file storage space in OneDrive, as a part of their Office 365 subscription. This is online cloud storage and can be accessed from a multitude of devices: Windows PCs, Macs, via the web, and from a smart phones or tablets devices. To access OneDrive on Windows, open File Explorer and locate OneDrive on the file list located on the left pane. You will need to sign in using your O-Key account. To access OneDrive on Mac, download the OneDrive app from the App Store. Once downloaded, sign into the app to view OneDrive in Finder. To access on a smart phone or tablet download the OneDrive app. Once the app is downloaded, sign in to view your files. For iOS, download from the App Store. For Android, download from the Google Play Store. To access OneDrive via the web, go to cowboymail.okstate.edu, click the App launcher in the top left, and select “OneDrive”. To learn more about OneDrive and its functions, you can check out the blog post created by Bronson Lewis, Extension Support Specialist, DASNR IT, titled “Sync Files with OneDrive in Windows”.
- Employees get 500 MB of personal network drive space, referred to as your “Home Drive.” You can access it from an office computer or, when off campus, through OSU’s Virtual Private Network (VPN). When on campus, the Home Drive can be accessed through File Explorer (Windows) or Finder (Mac). Look for the home drive folder. If you’re not on campus, connect using the OSU VPN. After connecting to the VPN, you will be able to view through File Explorer (Windows) or Finder (Mac). View accessing instructions
Alternative Recommended Solutions
Another solution for backing up your data is a service named iDrive. iDrive has been recommended by Extension Computer Support Specialists for some time now and can offer data backup solutions for users who are not on campus and want to have the security of an online backup. Apart from their competitive pricing, iDrive has many features that help to make it a good, overall backup solution for any type of user, including:
- Continuous Data Protection (CDP) – automatically backs up changes made to files
- Support for Windows, OS X, Android, iOS, and various NAS devices
- Snapshots – restore data to a specific point in time
- IDrive Express – a two-way physical shipment service for faster backups and restores
- Sync – IDrive links all of your devices so whenever a file is updated, it is available on all linked devices
- Share files with anyone
- Ability to back up to local drives
Please note that while iDrive does have a “free” option, most of their support does come with a yearly service fee.

Offline backups
These are great options, but what about those times where you can’t get on the network or internet to access your files? We can follow the example of the client I mentioned earlier – and use an external hard drive. Not all external storage options are created equal. Aside from price, drives vary in speed, portability and storage. Choosing the perfect external drive is best settled by answering one simple question: How does this external drive compare to available network backup solutions (mentioned earlier in this article)? If you need help answering this question or are confused by the options, discuss your situation with a Computer Specialist in DASNR IT or your departmental IT Specialist. More options are available from the links provided below too.
Just do it!
Keeping your data properly archived adds a layer of protection to your sensitive files from malicious activity and it allows for recovery in the event of equipment failure. If you have not initiated a data backup plan, just do it!
Resource URLs
- OSU Online Storage: https://it.okstate.edu/services/online-file-storage-employees/index.html
- PCMag: https://www.pcmag.com/picks/the-best-external-hard-drives
- iDrive: https://www.idrive.com/
Silver Sparrow: What is it and How to remove it
Mike Lane – DASNR IT
February 24, 2021

What is Silver Sparrow?
In February researchers at Red Canary announced that a “new” macOS malware strain had been discovered, naming it “Silver Sparrow”. As of February 17th, the malware had been detected in over 29,000 macOS devices across 153 countries; a majority of the infections reside in the US, UK, Canada, France and Germany.
Researchers from VMware, Carbon Black and Malwarebytes found that Silver Sparrow has one interesting characteristic: it has no payload which would be the resulting action from an infection. However, this does not rule out a future attack as there appears to be “repeated hourly updates”. Red Canary’s Tony Lambert writes:
“…the ultimate goal of this malware is a mystery. We have no way of knowing with certainty what payload would be distributed by the malware, if a payload has already been delivered and removed, or if the adversary has a future timeline for distribution. Based on data shared with us by Malwarebytes, the nearly 30,000 affected hosts have not downloaded what would be the next or final payload.”
Currently Apple is in the process of “Eradicating” the new strain; details are forthcoming.
Two versions of Silver Sparrow have been discovered: one version consists of a binary affecting Intel based Macs only and a second version affects both Intel and M1 architectures.
How to remove Silver Sparrow?
Here are some questions to help determine “if” your Mac has been infected:
- Were you prompted by a website to download a software package and/or update?
- Was this something that you had no intention of downloading/installing until you were prompted to do so from a website?
- Was the file named something similar to “update.pkg” or “updater.pkg”?
If you answered “yes” to any of the above questions, some suspicion is justified. While there are no current outward signs of infection based upon observable behavior, Silver Sparrow is known to place certain files on the Mac system. Red Canary notes that four files are a tale-tell sign that your system may be infected:
- ~/Library/._insu (empty file used to signal the malware to delete itself)
- /tmp/agent.sh (shell script executed for installation callback)
- /tmp/version.json
- /tmp/version.plist
MalwareBytes can find and clean Silver Sparrow. If you are interested in installing or having MalwareBytes installed to your university-owned computer, please contact your departmental IT Specialist, a member of DASNR Information Technology, or the IT Helpdesk. Below are additional resources you may find beneficial:
* https://appleinsider.com/articles/21/02/20/more-malware-found-to-target-apple-silicon-macs
* https://appleinsider.com/articles/21/02/17/first-apple-silicon-m1-malware-discovered-in-the-wild
* https://appleinsider.com/articles/21/02/22/apple-has-taken-steps-to-eradicate-mysterious-malware-strain
* https://redcanary.com/blog/clipping-silver-sparrows-wings/
* https://lifehacker.com/find-and-remove-the-new-silver-sparrow-macos-malware-1846324908
* https://www.macobserver.com/news/how-find-silver-sparrow/
* https://blog.malwarebytes.com/mac/2021/02/the-mystery-of-the-silver-sparrow-mac-malware/
Multi-Factor Authentication

What is Multi-factor Authentication (MFA) and why do I need it?
MFA enhances the traditional user ID/password combination that has been used for years. Using MFA increases account security by requiring a user to provide multiple forms of identification, like something you know (a password) and something you have (such as a mobile device). Because both are required for a successful login, this protects an account by reducing the likelihood of an attacker successfully logging in. The attacker would need to know the user’s password and have access to a physical device that provides the secondary factor in order to complete a successful logon.
All applications that use the Central Authentication Service (CAS) will be required to use MFA. If your application logon looks like the picture to the right, you will be required to implement MFA according to the following dates. If you have already implemented MFA, you can disregard this email.
When will MFA be required?
Employees (Non-student) Sept. 16, 2020 by 5 p.m.
Retirees Sept. 16, 2020 by 5 p.m.
Students Oct. 16, 2020 by 5 p.m. – Communications forthcoming
Graduates Oct. 16, 2020 by 5 p.m. – Communications forthcoming
The first campus-wide communication was sent in November 2019. Information Technology Coordinators have been communicating on a regular basis to their users asking for voluntary participation.
FAQ
Why is Multi-factor Authentication (MFA) important to OSU?
Securing OSU’s computing environment is more important now than ever. Historically, one of the most often used methods to compromise computer systems is through individual’s user ID’s and passwords.
How do I get started?
A user can log into the OSU Duo portal using their O-Key username and password. Once they log in they are able to sign up for Duo, add a new device, or manage existing devices.
Where is Multi-factor Authentication (MFA) available?
Campuses
- Oklahoma State University Stillwater
- Oklahoma State University Institute of Technology (Okmulgee)
- Oklahoma State University Tulsa
- Oklahoma State University OKC
- Connors State College
- Langston University
- Northeastern Oklahoma A&M College
- Oklahoma Panhandle State University
Roles
- Faculty
- Staff
- Students *
- Associates
- Alumni
*Accounts for people who have applied to any of the campuses but are not accepted are not covered under the license.
FAQ Continued
Need Help?
Contact the OSU IT Helpdesk
Phone: 405-744-HELP(4357)
Fax: 405-744-7861
Toll Free: 1-877-951-4836 (calls cannot be transferred)
Email: helpdesk@okstate.edu
Location: 421 Classroom Building
Walk-in hours are M-F 8 AM to 5 PM.
Resource URLs:
* https://it.okstate.edu/services/multi-factor-authentication/index.html
* https://it.okstate.edu/services/multi-factor-authentication/how-do-i-obtain-a-hardware-passcode-fob-for-use-with-multifactor-authentication.html
* https://it.okstate.edu/services/multi-factor-authentication/what-are-my-options-if-i-do-not-have-a-landline-device-and-my-mobile-device-cannot-connect-to-osu-network.html
Cyber Security and Your Personal Devices
Bring Your Own Device (BYOD) has become the standard instead of the exception for many organizations, with an estimated 70% of mobile professionals using personal devices for work-related activities. As to be expected, many businesses have been hesitant in allowing their employees to use personal devices due to concerns with security. As such, many companies have put in place tools to protect their sensitive data – but what can you do to protect the data on your personal device?
- Keep your software up to date: In 2017 one of the major types of cyber attacks came in the form of ransomware – both businesses and consumers alike were affected. One of the most important safeguards to prevent such attacks is by patching outdated software, both in operating systems and applications: enable “Automatic System Updates” for your device and make sure your web browser is updated too. These steps help to remove vulnerabilities that hackers can use to access your data through your devices.
- Use anti-virus protection: Anti-virus (AV) and anti-malware protection software is one of the main defenses to combat malicious attacks. This software helps to prevent viruses and malware from entering your device and compromising your data. Note: antivirus and anti-malware software is not 100% effective from every kind of attack. Due diligence is still necessary when using your device. Use software from trusted vendors and only run one antivirus/anti-malware tool on your device.
- Use a firewall: Similar to antivirus and anti-malware software, a firewall protects your device from malicious intent. It helps screen out unauthorized users (hackers), viruses, malware and other unauthorized activity by determining what traffic is allowed to enter your device. Windows Operating Systems (OS) and Mac OS X comes with their respective firewalls (Windows OS: Windows Firewall. Mac OS X: Mac Firewall).
- Use strong passwords: It cannot be overstated: strong passwords are crucial to online security! Passwords keep our accounts and networks safe from unwanted access by those with malicious intent. According to the National Institute of Standards and Technology (NIST) you should consider the following when creating and/or updating your password(s):
- Create/use a password with a minimum of 8 characters that should contain a least one lower-case letter, one upper-case letter, one number and a symbol. Your password(s) should not spell out actual words and should not be related to important information such as birthdays, anniversaries or locations
- Do not use the same password twice.
- Choose a password that is easy to remember.
- Do not leave your password hints out in the open and do not share your password with others.
- Change your password(s) often, at least once per year.
- If you plan to leave your computer or personal device, lock the screen and require a password for re-entry.
- Use two/multi-factor authentication: two-factor or multi-factor authentication is a service that provides additional layers of security to your accounts. This is achieved through many different channels, for example push notification, personal identification number (PIN) and finger print identification. For more information, click here.
- Use caution: It is easy to become distracted during our daily activities; however, one of the more common cyber security threats can be prevented simply by using caution. These threats can come in the form of email messages with links to websites, telephone calls from someone desperate, and even printed fliers tacked to bulletin boards advertising something free. Each of these are types of phishing attacks in which someone with malicious intent attempts to steal your personal information. Phishing attacks are highly effective and very lucrative for the scammer: in 2018 nearly 1 in 6 Americans lost money due to phone scams.
- Protect your personal identifiable information (PII): Personal Identifiable Information (PII) is any information that can be used by someone with malicious intent to identify or locate an individual. PII includes data such as a name, address, phone number, birthday, Social Security Number, IP and MAC addresses, location details etc. This data is easily available, especially with the “Always on” default settings in our modern devices and with our social media accounts. In 2016, Cifas, the UK’s leading fraud prevention service, released a video demonstrating just how easy it is to gather your data.
- Use your mobile device securely: According to Malwarebytes Labs, some ways to ensure protection of your mobile device are:
- Lock your phone with a password or fingerprint detection.
- Consider encrypting your data.
- Only install apps from trusted sources
- Keep your device updated
- Avoid sending personal or sensitive information over text message or email
- Use Find my iPhone (iPhone) or the Android Device Manager (Android) to prevent loss or theft
- Use an anti-malware app
- Backup your data regularly: Regularly backing up your data to a secure source is not just a good idea to protect your data from cyber-attacks, but to also a good practice to prevent data loss in the event that there is a hardware failure on your device. Using resources such as iCloud (iOS/MacOS), OneDrive (Windows OS/ MacOS X 10.12 or later) and Backup and Sync (Android) will help ensure that your data is regularly backup up. Another option is to store your data on an external Hard Drive (HDD).
- Do not use public WiFi without a Virtual Private Network: By using a VPN, the traffic between your device and the VPN server is encrypted. This means it’s much more difficult for a cybercriminal to access your data. If you do not have a VPN, use your cell phone network.
Additional information and helpful links:
Microsoft Teams
Overview
Microsoft Teams is a cloud-based communications platform and part of the Office 365 suite. Teams provides a project group with many tools: a conversation and chat space, video meetings, and file storage. As part of Oklahoma State’s Microsoft license, Teams is free to use as an employee of OSU.
Features
MS (Microsoft) Teams offers you the ability to have a group chat, online meetings, calling and web conferencing, thereby allowing your team to more effectively communicate.
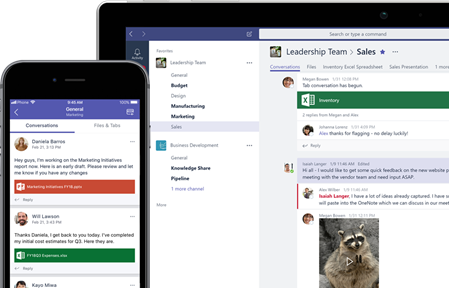
In Teams you can work together by collaborating on files with built-in Office 365 apps like Word, Excel, PowerPoint, and SharePoint. You can customize your workspace by adding in your favorite Microsoft Apps and third-party services such as OneDrive.
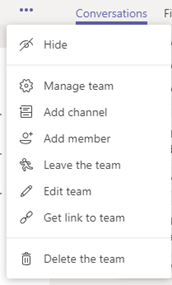
Administrators of the team can control membership and manage team information and security by clicking on ellipses (next to the team name):
If you are interested in learning more about Microsoft’s hub
for teamwork in Office 365, visit https://products.office.com/en-us/microsoft-teams/group-chat-software
.
FAQs
Q: Is
Microsoft Teams Free to use as an Employee at OSU?
A: Yes,
Microsoft Teams is free to use as an Employee of OSU.
Q: How do I
access Microsoft Teams?
A: The main ways to access Microsoft Teams is either through the Desktop standalone App, via the web, or through the Mobile App. Shown below are basic instructions:
Accessing Microsoft Teams – Standalone App
1. Start Teams.
- In Windows, click Start > Microsoft Corporation > Microsoft Teams.
- On Mac, go to the Applications folder and click Microsoft Teams.
- On mobile, tap the Teams icon.
2. Sign in with your Office 365 username and password.
Accessing Microsoft Teams – via the Web
1. Open a web browser (such as Microsoft Internet Explorer, Microsoft Edge, Mozilla Firefox, Google Chrome, Apple Safari, etc.) and visit Cowboy Mail (cowboymail.okstate.edu)
2. Log in using your OSU credentials.
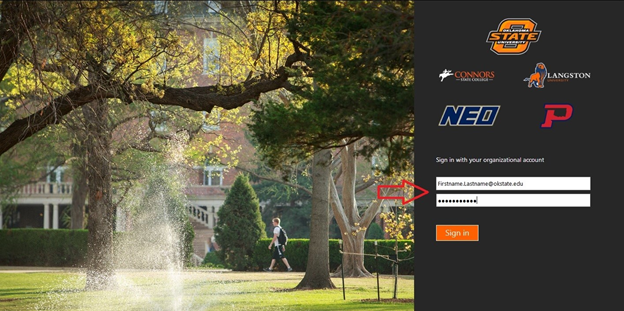
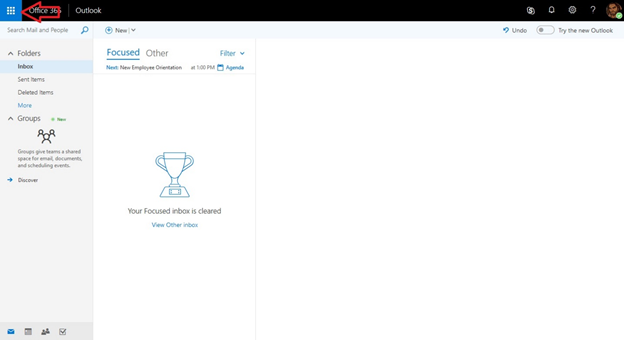
3. Once in CowboyMail, Click on “Apps” menu. The Apps Menu is the blue square with nine (9) white dots, located in the top left hand corner.
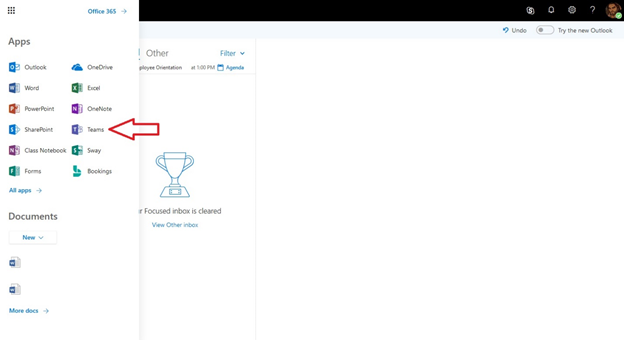
4. Once the Apps menu has opened, click on Teams.
5. From here, you will be redirected to Microsoft Teams. You will see team names for those teams to which you have access.
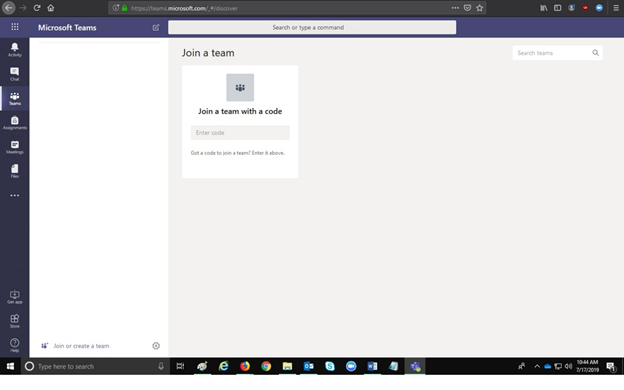
*NOTE* If you have previously logged into Microsoft Teams, and are attempting to log in again; you may be required to sign in using your OSU Credentials once again.
Accessing Microsoft Teams – Mobile App
- Go to the App store on your mobile device
(Apple App Store, or Google Play Store)
- Search for Microsoft Teams
- Once the Microsoft Teams App has been
downloaded and installed; Log in using your
OSU Credentials.
Q: How do I
setup a ‘team’?
A: Listed
below are the detailed instructions on how to setup a ‘team’.
- Login to https://okey.okstate.edu.
- From the left-hand navigation, select “Microsoft Groups”:
- Select “Create a new group as an employee”.
- Complete the form then click “Create Group”. After approximately one business day, the group is created and the team is available in Microsoft Teams.