Cyber Security and Your Personal Devices
Bring Your Own Device (BYOD) has become the standard instead of the exception for many organizations, with an estimated 70% of mobile professionals using personal devices for work-related activities. As to be expected, many businesses have been hesitant in allowing their employees to use personal devices due to concerns with security. As such, many companies have put in place tools to protect their sensitive data – but what can you do to protect the data on your personal device?
- Keep your software up to date: In 2017 one of the major types of cyber attacks came in the form of ransomware – both businesses and consumers alike were affected. One of the most important safeguards to prevent such attacks is by patching outdated software, both in operating systems and applications: enable “Automatic System Updates” for your device and make sure your web browser is updated too. These steps help to remove vulnerabilities that hackers can use to access your data through your devices.
- Use anti-virus protection: Anti-virus (AV) and anti-malware protection software is one of the main defenses to combat malicious attacks. This software helps to prevent viruses and malware from entering your device and compromising your data. Note: antivirus and anti-malware software is not 100% effective from every kind of attack. Due diligence is still necessary when using your device. Use software from trusted vendors and only run one antivirus/anti-malware tool on your device.
- Use a firewall: Similar to antivirus and anti-malware software, a firewall protects your device from malicious intent. It helps screen out unauthorized users (hackers), viruses, malware and other unauthorized activity by determining what traffic is allowed to enter your device. Windows Operating Systems (OS) and Mac OS X comes with their respective firewalls (Windows OS: Windows Firewall. Mac OS X: Mac Firewall).
- Use strong passwords: It cannot be overstated: strong passwords are crucial to online security! Passwords keep our accounts and networks safe from unwanted access by those with malicious intent. According to the National Institute of Standards and Technology (NIST) you should consider the following when creating and/or updating your password(s):
- Create/use a password with a minimum of 8 characters that should contain a least one lower-case letter, one upper-case letter, one number and a symbol. Your password(s) should not spell out actual words and should not be related to important information such as birthdays, anniversaries or locations
- Do not use the same password twice.
- Choose a password that is easy to remember.
- Do not leave your password hints out in the open and do not share your password with others.
- Change your password(s) often, at least once per year.
- If you plan to leave your computer or personal device, lock the screen and require a password for re-entry.
- Use two/multi-factor authentication: two-factor or multi-factor authentication is a service that provides additional layers of security to your accounts. This is achieved through many different channels, for example push notification, personal identification number (PIN) and finger print identification. For more information, click here.
- Use caution: It is easy to become distracted during our daily activities; however, one of the more common cyber security threats can be prevented simply by using caution. These threats can come in the form of email messages with links to websites, telephone calls from someone desperate, and even printed fliers tacked to bulletin boards advertising something free. Each of these are types of phishing attacks in which someone with malicious intent attempts to steal your personal information. Phishing attacks are highly effective and very lucrative for the scammer: in 2018 nearly 1 in 6 Americans lost money due to phone scams.
- Protect your personal identifiable information (PII): Personal Identifiable Information (PII) is any information that can be used by someone with malicious intent to identify or locate an individual. PII includes data such as a name, address, phone number, birthday, Social Security Number, IP and MAC addresses, location details etc. This data is easily available, especially with the “Always on” default settings in our modern devices and with our social media accounts. In 2016, Cifas, the UK’s leading fraud prevention service, released a video demonstrating just how easy it is to gather your data.
- Use your mobile device securely: According to Malwarebytes Labs, some ways to ensure protection of your mobile device are:
- Lock your phone with a password or fingerprint detection.
- Consider encrypting your data.
- Only install apps from trusted sources
- Keep your device updated
- Avoid sending personal or sensitive information over text message or email
- Use Find my iPhone (iPhone) or the Android Device Manager (Android) to prevent loss or theft
- Use an anti-malware app
- Backup your data regularly: Regularly backing up your data to a secure source is not just a good idea to protect your data from cyber-attacks, but to also a good practice to prevent data loss in the event that there is a hardware failure on your device. Using resources such as iCloud (iOS/MacOS), OneDrive (Windows OS/ MacOS X 10.12 or later) and Backup and Sync (Android) will help ensure that your data is regularly backup up. Another option is to store your data on an external Hard Drive (HDD).
- Do not use public WiFi without a Virtual Private Network: By using a VPN, the traffic between your device and the VPN server is encrypted. This means it’s much more difficult for a cybercriminal to access your data. If you do not have a VPN, use your cell phone network.
Additional information and helpful links:
Password and Account Protection
Online access provides you with incredible opportunities: check a bank statement, pay a mortgage, make a credit card payment, check a credit score, and order just about anything then have it delivered to your house! But each of these tasks requires you to login to a website or app, and keeping each account safe is of critical importance. A strong password for each account is fundamental.
 Internet Security System
Internet Security System
What makes a “strong” password? It begins with the password length: the longer the password the longer it takes for a hacker or hacker’s computer to guess or crack the password, and that time dramatically increases for each additional character or number. It is a balance, however, since a password that is too long may be difficult to remember (which defeats the purpose of a strong password). A good password length is 8-10 characters.
A common way to make strong passwords easy to remember is by using a passphrase. Using random words that don’t fit with each other helps increase the uniqueness of the password. This well known XKCD comic helps demonstrate a strong password:
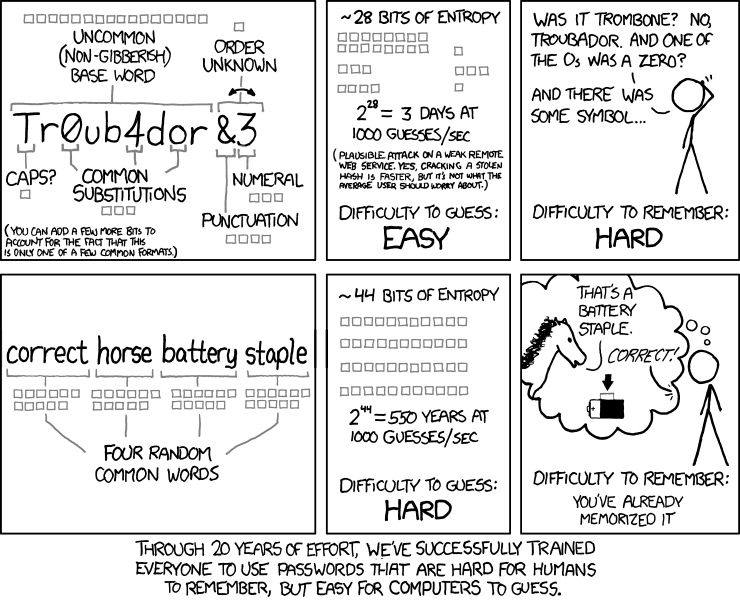
Of the many password practices, several are things we really shouldn’t do. If you make a strong password but use it on every website, a breach of security on any of the websites could cause your password to be known and this weakens your password. Every password should be unique to the account and it should not be reused for another account. Another ill-conceived practice is using names of pets, people, or notable dates as a password. These are also easy to crack for a password cracker. In addition to not using names or dates, do not use the same base password then change a number or two at the end. This practice has the same problem as using the same password on each of these sites.

Finally, one other step you can take to secure your accounts is using multi-factor authentication (MFA). A common form of multi-factor authentication is two-factor authentication. Two-factor authentication increases the security by requiring two authentication factors: The first factor is usually a knowledge factor (the password that you know) and the second factor is a possession factor – something physical that you have such as an ID card, security token, or smartphone. In multi-factor authentication, a the third common factor is the inheritance factor (also known as the biometric factor). There are other authentication factors, such as location and time, but these are three of the most common. Having an account requiring two of these factors makes breaking into your account all that much harder as hackers since they would need two things from you, not just your password.
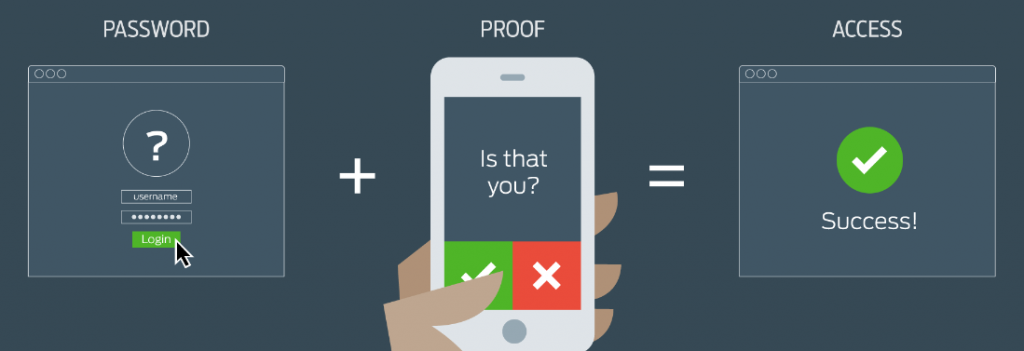
Oklahoma State University also has a two-factor authentication option for logging into all the websites that use your OKEY login. For more information see https://it.sp.okstate.edu/itservices/4help/guide.aspx?guideName=STW-IT_Duo_Setup_And_Use. Start your setup for Multi-factor Authentication at https://apps.okstate.edu/duo_portal.