What App? – Vetting Apps for Your Phone and Tablet

Picture it. Oklahoma, 2025. It’s summer. It’s hot, humid, and the cicadas are deafening. I’m scrolling through emails, trying to stay cool with a tall glass of iced tea and my phone rings. It’s my mother-in-law and she’s got a story to tell. International travel, deadlines closing in, eVisa? The government sanctioned app she had to use for a new eVisa system wasn’t available for her mobile phone, so she downloaded another app that claimed it could do the same thing – for nearly 4x the original fee. Suddenly that iced tea wasn’t so refreshing.
Mobile devices, like cell phones and tablets, have app stores with seemingly endless app options. These options can be difficult to navigate: once you think you have the app you need and start setting up yet another account to use the app, you realize that maybe that wasn’t the legitimate one. Was it the first option in the Apple App store? Was it the green one or the blue one in the Google Play store? They both look the same, or do they? Here are a few tips to keep you, your data, and your wallet safe.
Check the Developer
Notice the app publisher. Well-known companies or verified developers are more trustworthy. Developers who want to steal your information and your money do not have a large web presence or may not have a web presence at all. For example, them may have a Facebook page or Instagram account only.
Read Reviews and Ratings
Check for consistent, positive reviews and high ratings. Be cautious of apps with very few reviews or overly generic 5-star ratings—they might be fake. Users who post mid to low reviews are often more specific about the issues they experience and even post warnings for others if they believe the app is misrepresenting or malicious.
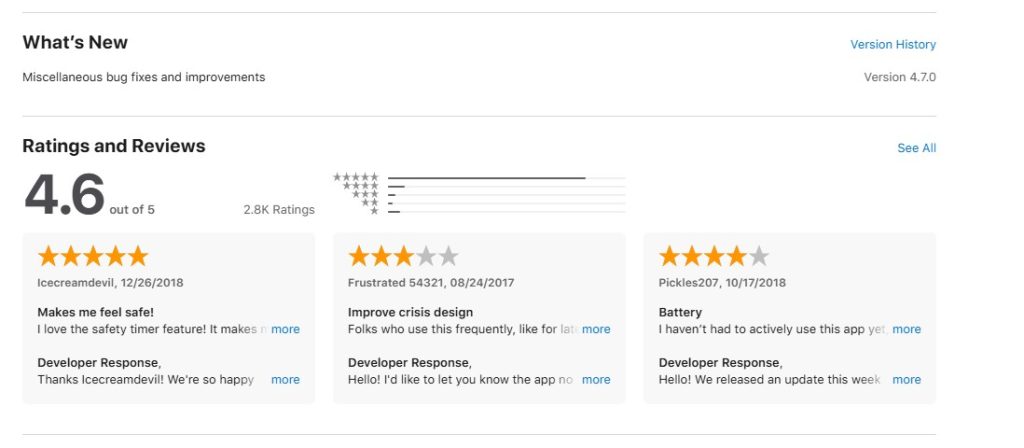
Check Update History
Legit apps are regularly updated to fix bugs and improve features. A list of fixes and added features are usually listed on the app’s store page along with dates these were applied. Links to the developer website explaining these changes may be included. If the app hasn’t been updated in a long time, it might be abandoned or unsafe.
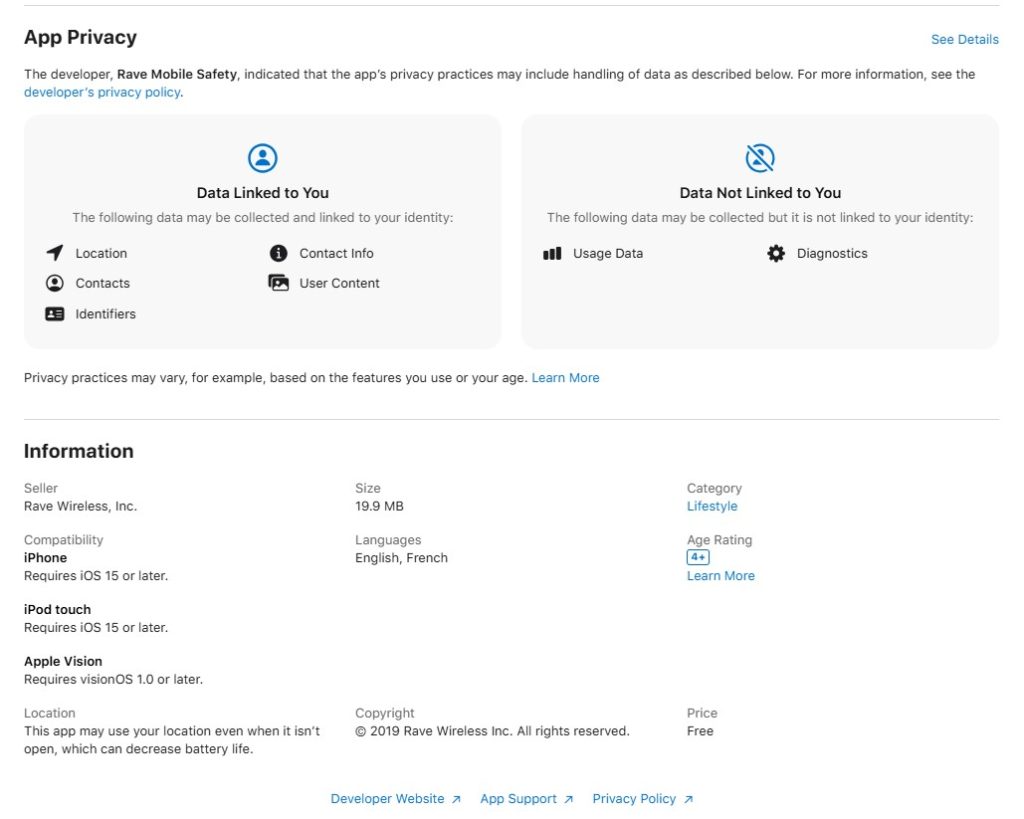
Review Permissions
Be wary of apps asking for unnecessary permissions (e.g., a flashlight app asking for access to your contacts). You can review permissions before installing the app and adjust those permissions during the setup or after the app is installed. This information is found under App Privacy if using the Apple Store, and Data Safety if using the Google Play store. Unnecessary access to certain features and data can allow malicious apps to access and take information stored on your phone or tablet. This information can be sold to other malicious actors by the developer.
Visit the Official Website
Check if the app is mentioned on the company’s official website. If a website directs you to their app, make sure the information in the app store matches the information on the website. Developer or company name, contact information and company logo should be consistent in both places. If the app is promoted through shady websites or social media ads only, be cautious.
App Store Protections
Download only from official app stores (Google Play Store, Apple App Store). Avoid downloading APKs from third-party sites unless you’re absolutely sure they’re safe.

Search for Red Flags
Look up the app name + “scam” or “malware” online. If others have had bad experiences, you’ll likely find warnings. Keep an eye on the news for stories of data breaches through apps or companies who have had a cyberattack. If you already have the app installed, remove your information from the app and uninstall it until it’s proven safe to use.
If you still aren’t sure about the app you’re about to click on, contact us in Agriculture IT or ask a trusted friend or family member for help investigating the app or completing your task another way. My mother-in-law did go on her trip. The government-sanctioned app wasn’t supported on her phone’s software version, but we found a way to upload all the necessary information on the government’s website and paid the exact fee.
AI and Cybersecurity: Smarter Tech, Bigger Risks

Introduction
As artificial intelligence becomes more prevalent in our lives and workflows, it’s not just a neutral tool that can help us be more productive – it’s also an evolving battlefield of attack vs defense. For National Cybersecurity Awareness Month, the question isn’t just “how do we use AI safely?” but also “how might cybercriminals weaponize AI against us?”
Recent trends suggest that AI-based attacks are not hypothetical future threats — they are happening now. From highly convincing phishing attempts and deepfake videos to prompt-injections and AI-assisted reconnaissance, cybercriminals are experimenting and scaling up their attacks. A 2025 survey found that 74% of IT leaders say they have definitely experienced an AI-related breach, and 98% believe they’ve likely had one already — yet only 32% are using dedicated defenses for AI systems.
As attackers leverage AI for speed, scale, and evasion, defenders must react not just with tools, but with awareness. In this article, we’ll unpack how AI is reshaping the cyber threat landscape and share strategies to stay ahead.
While AI can amplify cyber threats, it’s also one of the most powerful tools available to defend against them. Modern cybersecurity teams are already using machine learning and generative AI to detect, predict, and respond to threats faster than humans ever could. The promise of AI in security comes down to one word: scale.
The Promise
Faster Threat Detection
AI-driven analytics can process billions of network events per second, identifying patterns that would be invisible to human analysts. In 2024, Microsoft reported that its AI threat detection systems analyze over 65 trillion signals daily, helping it spot emerging attack trends and stop intrusions in near real-time.
Predictive Defense
Unlike legacy security systems that only react to attacks, AI models can predict potential vulnerabilities by studying known exploits, code changes, and behavior signatures.
Automated Response and Recovery
AI doesn’t just detect threats — it can act on them. Through automated incident response systems, AI can quarantine infected devices, block malicious IP addresses, or revoke compromised credentials in seconds, reducing down time and limiting damage.
Enhanced Human Decision-Making
AI isn’t replacing IT Security experts — it’s augmenting them. By handling repetitive monitoring and triage tasks, AI allows analysts to focus on complex investigations, strategy, and policy decisions. It effectively acts as a “force multiplier” for human defenders.
What does it mean?
In the cybersecurity world, AI will enable security experts to focus on more complex tasks, strategies, and policy decisions, while working in the background to spot and stop potential threats in a proactive way, instead of only relying on reacting to an attack when it may be too late.
The Risks

For all its defensive promise, AI also introduces new and serious risks. Every advancement in automation, scale, and speed can be turned around and used by attackers. As organizations adopt AI for security, they also need to account for how AI systems themselves — and the data they rely on — can become targets.
AI-Powered Threats
Attackers are using AI to make their operations more effective. Generative AI can craft convincing phishing emails, fake personas, or malicious code at scale. In 2024, a deepfake voice scam in Hong Kong reportedly tricked a finance employee into transferring $25 million to criminals posing as the CFO — a stark example of AI-enabled fraud.
Prompt Injection and Model Manipulation
Generative AI systems can be tricked into performing unintended actions through prompt injection — malicious inputs designed to override safety rules or extract sensitive information. Attackers can embed these instructions in text, code, or even web content that the AI processes automatically.
Poisoned or Biased Training Data
AI models trained on compromised data can produce skewed or dangerous results. Attackers may inject false or misleading data into training pipelines, leading to data poisoning attacks that degrade the accuracy of threat detection systems or hide malicious activity. In cybersecurity contexts, poisoned datasets could cause an AI system to “ignore” specific attack patterns altogether.
Over-Reliance and False Confidence
AI tools can create a false sense of security. If organizations treat AI outputs as infallible, they risk missing sophisticated threats or misjudging incidents. Automation without oversight can also lead to cascading failures — like automated blocking systems taking down critical infrastructure due to a misclassification.
Security Best Practices for AI Use
Even if you’re not in IT, you interact with AI systems daily — chatbots, writing tools, automated assistants, and analytics dashboards. The same security mindset that applies to email and social media now applies to AI, too.
Think Before You Share
- Just like when browsing the web or posting to social media, never enter confidential, personal, or proprietary information into AI tools unless your organization has explicitly approved them.
- Treat AI chatbots like public websites — anything you type could be stored, reviewed, or reused to train models.
- If in doubt, ask your IT or compliance team before sharing sensitive data.
Verify Before You Trust
- AI can sound confident but still be wrong. Always double-check facts, links, or recommendations generated by AI before taking action.
- Watch out for AI-assisted scams — phishing emails or messages may now use perfect grammar, realistic names, and context-aware details.
Use Official Tools Only
- Stick to university-approved AI tools and accounts. “Shadow AI” — using unapproved apps like free AI chatbots or extensions — can expose sensitive data. Copilot is available with the university’s Office 365 subscription.
- If you need an AI tool for your workflow, request approval instead of finding your own workaround.
Watch for Deepfakes and Impersonations
- Be cautious with unexpected calls, videos, or messages that seem slightly off — even if they use real voices or names.
- Always verify through a second channel (like a known phone number or internal messaging) before acting on instructions involving money, credentials, or private info.
Keep Credentials Safe
- Never paste passwords, API keys, or tokens into AI prompts or shared documents.
- Use password managers and multi-factor authentication for all accounts connected to AI tools.
Report Anything Suspicious
- If an AI tool behaves oddly — such as revealing unexpected data, asking for private info, or giving risky instructions — report it to IT right away.
- Early reporting helps prevent larger security incidents.
Stay Informed
- Keep up with short internal security briefings or awareness newsletters. AI evolves quickly — knowing the latest scams and university guidelines keeps you ahead.
Conclusion
If you wouldn’t email it to a stranger, don’t feed it to an AI.
If it seems too real, verify it twice.
If something feels off, report it.
If you have any questions or require more information about the security involved with AI, please contact your Computer Support Specialist.
https://hiddenlayer.com/innovation-hub/top-5-ai-threat-vectors-in-2025
https://www.microsoft.com/en-us/security/security-insider/threat-landscape/microsoft-digital-defense-report-2024
https://www.ft.com/content/b977e8d4-664c-4ae4-8a8e-eb93bdf785ea?utm_source=chatgpt.com
Beyond the Shadows: Understanding and Managing Shadow IT in Modern Workplaces

Overview
Shadow IT, the use of unsanctioned technology within organizations, has emerged as a double-edged sword in today’s digital environments: While it can foster innovation and productivity, it also introduces serious risks such as data breaches, compliance violations, and integration challenges. This article explores the concept of Shadow IT, its causes, risks, potential benefits, and practical strategies for mitigating associated threats.
Introduction
On the OSU-Stillwater campus, our Enterprise IT department has policies governing use of the campus network. For example, connecting to the OSUGUEST wireless network first requires the user provide contact information before internet access is provided to the device. In this case policies helps limit liability for the individual user and for other users on the same network. Some policies, however, may not be fully understood and seen as obstacles to intended users. In an attempt to enhance productivity, employees may find detours to bypass formal IT processes. This phenomenon, commonly referred to as Shadow IT, refers to the use of hardware, software, or services without the knowledge or approval of the central IT department (Syteca, 2023).

Shadow IT exists in our homes too. Examples include the installation of unauthorized (or unintended) apps on personal devices and devices we’ve forgotten but are still connected to our home’s network. Shadow IT in our homes creates hidden vulnerabilities (Group-IB, 2023).
Forms of Shadow IT
- Unsanctioned IT Assets – Employees bypass procurement procedures, introducing devices or software (e.g., Bring Your Own Device – BYOD) without IT input and oversight.
- Forgotten Infrastructure – Old laptops, phones, or network equipment that were never decommissioned remain connected to networks, holding sensitive data.
- Misconfigurations – IT assets meant to remain accessible only for internal purposes are inadvertently exposed to the public internet.
Risks of Shadow IT
The presence of Shadow IT in organizations introduces several significant risks:
- Data Loss and Leakage – Unauthorized apps often lack encryption or controls, exposing sensitive data.
- Compliance Violations – Shadow IT undermines regulatory requirements such as GDPR or HIPAA.
- Ineffective Security Patching – Systems could remain outdated and vulnerable to compromises.
- New Attack Vectors – Unmanaged apps and devices provide potential entry points for attackers.
- Integration Challenges – Unauthorized solutions may create silos and inefficiencies.
Benefits of Shadow IT
Despite the risks, Shadow IT can offer limited organizational value:
- Productivity Gains – Employees adopt faster or more effective tools when sanctioned systems fall short.
- Identifying Gaps – Adoption of unsanctioned solutions often highlights shortcomings in official IT tools and policies.
Mitigation Strategies
Organizations can recognize Shadow IT and reduce its risks by:
- Implementing clear IT policies – Establishing guidelines for procurement and acceptable use.
- Improving communication – Encouraging employees to share their tech needs with IT.
- Enhancing visibility – Using monitoring tools to detect unauthorized devices and apps.
- Regular audits – Identifying lost (or forgotten) infrastructure or misconfigured assets.
- Education and awareness – Training employees on security risks and compliance requirements.
Conclusion
Agriculture IT understands the purposes for Shadow IT because it reflects the evolving needs of our users in their digital work spaces and homes. We invite conversations about this topic as we view them to be an opportunity to improve our responsiveness, governance, and user engagement. Hopefully, together, we can be proactive and foster both innovation and security.
References
Hook, Line and Sinker: Don’t get reeled in by phishing scams!
If an email promises you free gift cards, asks you to verify your account, or insists that your bank will close your account in 24 hours: congratulations, you’ve just been invited on a phishing trip. But unlike real fishing, the only thing getting caught is you. Phishing is one of the most common and effective tricks cybercriminals use to steal personal information. In this article, we’ll cover what phishing is, and most importantly, what you can do to avoid taking the bait.

So, what exactly is phishing? Put simply, phishing is a form of cybercrime where attackers send deceptive messages that appear to come from trusted sources. These messages, most often an email or text, are designed to look like they’re from your bank, employer, or another authoritative organization. They often use urgent language such as “immediate action required” or “your account will be suspended” to create panic and push you to respond without thinking.
The goal is simple: to get you to click on a link, visit a fake website, and hand over sensitive information like login credentials or financial details. Once you do, cybercriminals have exactly what they need to compromise your accounts.
While anyone with an email address can be a target, phishing is especially dangerous in the workplace. Why? Because cybercriminals aren’t just after your Netflix password; they’re after sensitive data, which businesses store in bulk: financial records, client information, employee records, etc.
This is why employees are often the primary target of phishing attacks. The reality is that most employees are juggling tasks, skimming through emails, and instinctively trusting messages that look familiar, and that’s exactly what makes them such a prime target. One convincing email is all it takes.

So how can you spot a phishing attack and keep your data secure? It starts with understanding what these messages look like. If you notice an email that is asking you to take immediate action, there are a few key things to check. First, check the sender’s email address, it might look close to legitimate but is just off enough to raise suspicion. Second, pay attention to the content of the message. Many phishing emails include poor grammar, vague greetings like “Dear Customer,” or unexpected attachments. Next, be cautious of any links or buttons in the email. Even if they appear to go to a familiar website, they could take you to a fake page designed to steal your information. Lastly, consider whether the email is asking for sensitive information that a legitimate sender would never request over email. By staying alert of what phishing looks like, you can avoid falling into a trap and keep both your personal and company data safe.
Protecting yourself from phishing starts with a few smart habits. If an email feels urgent or asks for sensitive information, pause before clicking. Check the sender’s address, hover over links to see where they lead, and avoid downloading unexpected attachments. Using strong passwords, enabling multi-factor authentication, and keeping your software up to date all add extra layers of security. If something seems suspicious, report it to your IT team. Remember: when an email says “urgent” or “act now,” take a moment to pause, think, and report. Together, we can make our workplace safer.