Reusing Adobe Connect Recordings in Adobe Connect
Adobe Connect is a great tool for online collaboration and has become a standard tool across DASNR, allowing for many to attend meetings, in-services and training’s without having to use funds from their travel budget. However, there may be features yet to be discovered
I discovered a new feature the other day when I was asked to monitor a training session. Basic request, right? It became challenging when the presenters needed to use a segment of a previously recorded Adobe Connect session due to an absent co-presenter. At first, I didn’t think this was possible but I began searching for information anyway. After some digging, I discovered it was possible and was able to successfully use the recording in a live Adobe Connect session. These are the steps I took to make it happen.
First, access the Adobe Connect recording you wish to reuse. It should be noted, if you were not a Host of the original session, you will need to request permissions from the original Host. Once you have located the recording, select “Make Offline.” This will open the recording with a series of setting selections. I used the default settings. After you select “Proceed with Offline Recording” you will be able to save the file to your computer.
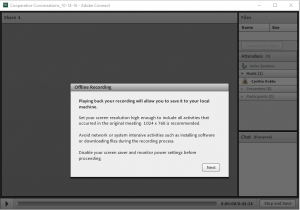
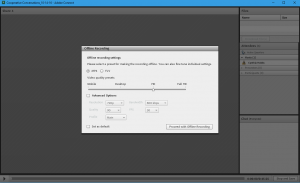
The saving process will take the duration of the original recording if you want to save all of it. Also, if you only want to save a segment, you cannot skip to that part. However, you can stop the recording once you have what you want. To stop and save, simply click “Stop and Save” in the lower right corner of the screen. Then click “OK” on the pop up.
You are now ready to insert the video into a new Adobe Connect session. This can be done the same way you load a PowerPoint. Simply click “Share My Screen, navigate to the MP4 file you are wishing to use and you are ready to go!
~Cynthia Hobbs
Cybersecurity Awareness Month, October 2016 – Potentially Dangerous Apps
Have you considered how the internet is a worldwide playground where kids of all ages – 3 to 103 – can play, mostly unsupervised? On this playground, we can interact through real-time message apps or through post and respond methods. We keep in constant contact with friends and provide updates on our latest travels. While in this virtual playground strangers can initiate conversations. This article provides an overview of some popular social media apps used by teens and how parents can more closely supervise their kids while on the “playground”.
All users, especially kids and teens, should be aware of oversharing information – providing too much personal information that can lead to unintended consequences. But some social media apps encourage this behavior and facilitate a dangerous level of secrecy and anonymity for kids and teens. These apps have two basic troubling characteristics:
* Users can meet and connect with strangers outside their parents knowledge.
* The anonymity allows users to act with impunity and without fear of being identified.
Unfortunately the list of apps that fit into this category grows quickly; the following are some of the more popular apps used by teens:
* Kik
* Tinder
* YikYak
* Omegle
* MeetMe
* Whisper
* Ask.fm
* Blendr & Grindr
Some apps allow the teen to hide information that may have been collected (photos, screenshots, etc):
* KeepSafe
* AppLock
Parents should also be aware that many of the different gaming apps have in-game chatting or messaging. While these games can be harmless in the short term, players can be lulled into a false sense of security and give out personal information and even contact information.
How can parents stay engaged in the conversation with their teen?
* Talk to your child about the apps, not just the ones installed on their phone.
* Enable parental controls on the phone.
* Monitor their phone. Educate yourself about the installed apps.
* Install monitoring apps such Phone Sheriff or Secure Teen.
In general (kids, teens, and adults), when working with social media sites be aware of:
* Oversharing information. Providing too much online information can easily lead to identity theft.
* Friending strangers who pretend to be someone they are not.
* Location-based services that expose the user’s location and whereabouts.
Dwayne Hunter
Manager, DASNR Information Technology
Reference links:
Cybersecurity Awareness Month 2016: Passwords and Why Not to Use the Same One
We have been told to never use “easy” passwords and we should not use the same password for all our separate accounts. Well, why is all this fuss necessary? If the site is secure then what is the issue?
One problem is that most of the time hackers are not specifically targeting you or your account. They are focusing their hacking attempts on large companies with millions of usernames and passwords. Companies hacked and the number of accounts exposed in 2015:
- VTech (a toy tech company aimed for kids) 4.8 million
- T-Mobile – 15 million – names, addresses, SS#, passport numbers
- Scottrade – 4.6 Million – didn’t release info about it until 2 years later
- BlueCrossBS – 10 million – found out they had been hacked over a 2 year period
- CVS/Walgreens – Unknown Millions – Credit Cards, email, passwords, addresses
- LastPass (password manager) – data breach – passwords will need to be decrypted
- And most recently Yahoo revealed it was hacked in 2014 and the data breach affects 500 million users. They didn’t let anyone know about the breach until late September 2016.
Now, say they have hacked one of the companies above and you have an online account with one of these companies. More than likely you use the same username or email address to all or most of the other sites that require some form of authentication. In this case these hackers now have at least half of your security breached. With this stolen data, they can run automated programs to decrypt passwords. “Easy” passwords – those that do not contain both upper and lowercase letters, numbers, and special characters – are less challenging to crack and decrypt. For each of the decrypted passwords, the hackers have the full combination of username and password for your account. They assume most people will use the same username/password combination on other sites. So the hackers can attempt to use this newfound information on other sites, or they can sell the information to other hackers who will compromise your other online accounts, such as banking, shopping, bill paying, and personal/family insurance sites.
In some cases, companies don’t know they have been breached – sometimes for years. BlueCrossBlueShield didn’t discover their security breach for almost 2 years. Some companies will immediately disclose the data compromises but others may withhold the information for fear the news will negatively affect their business. When the news is not shared with account holders, the hackers have time to take the information and continue compromising accounts on other systems before users are made aware of the security breach. Identity theft is an unfortunate outcome of these circumstances. Imagine your headaches when all of your accounts are hacked at the same time!
Here are some tips on making a secure password that is easy to remember, but difficult to crack: 6 Tips For Creating An Unbreakable Password.
It is a good habit to use different passwords on your online accounts and frequently change the passwords. We all understand the inconvenience to have multiple passwords, but so is removing a fraudulent charge on your credit card or trying to recover from identity theft.
Mike Rasmussen
Computer Support Specialist, DASNR