State of Security – Cyber Security Awareness Month 2017
The State of Security 2017
October is the first full month of fall (and sometimes even feels like it), National Pizza Month, National Dental Hygiene Month (so brush your teeth after you finish your pizza) and National Cybersecurity Awareness Month. I would prefer to write about pizza, but since I work in IT, it think we will look at some cybersecurity issues.
Most areas of cybersecurity concern showed an increase through the first part of 2017. One area where that is not true has been exploit kits, which are software packages used by cybercriminals to attack computers. Three major exploit kits vanished in 2016: Angler, Nuclear and Neutrino. Angler disappeared following a series of arrest of Russian cybercriminals; it is unknown what prompted Nuclear and Neutrino to go offline. (One reason may be the patching of a number of Flash-related vulnerabilities and Oracle’s removal of the Java browser plugin, both of which were popular targets for exploit systems.)1 (more…)
Cybersecurity Awareness Month 2016: Ransomware and You
Ransomware is a term for malware that infects computers and attempts to extort money from the user by holding the files and data for ransom. In most cases, the data is encrypted in such a way as to make it no longer readable without the encryption key. The user is presented with instructions on how to pay the ransom, after which it should be possible to decrypt the files. Ransomware has existed for several years, but has exploded in popularity in the latter half of 2015 and the first half of 2016[1]. The primary reason for this explosion is that it has become the single most profitable form of malware in use; as an example, McAfee’s Q2 2016 security report told the story of a Russian gang of malware developers who made more than $120 million in the first six months of 2016. Even allowing for costs of distributing the malware, their profit was probably over $90 million[2].
With profits like that possible, it should be obvious both why cybercriminals are turning to ransomware and why the problem is likely to persist. There is great incentive for these criminals to continue developing new forms of ransomware and new ways of distributing the malware. Currently, variants of ransomware exist for Windows, Linux and MacOS systems; Windows variants are the most common, but the others are growing.
How can we protect our systems against ransomware? For ransomware, traditional antimalware tools don’t help us; they can remove the ransomware, but the files are still encrypted, and in most cases, cannot be decrypted without the key. We need to do two things to be secure:
- Don’t get infected; most of these attacks come through email or malicious advertising. For email, be extremely careful of attachments, especially zip files and Word documents, as Word macro installers for ransomware have started to show up in the wild. For malicious ads, update your system, especially Flash and Java, and run a good real-time protection antimalware.
- Have a good protected backup of your data. Online cloud backup is really the only protection against this type of ransomware. The various cloud backup services keep several versions of your data, so even if your files have been encrypted, it should be possible to restore unencrypted versions. They also are able to defend against most types of ransomware, so your backups should remain uncorrupted. If you don’t have this type of backup, then infection with ransomware will most likely result in complete data loss.
Some new variants of ransomware have the ability to copy themselves across network file shares, meaning that if one computer in an office became infected, soon all of them would also be infected. This also means that backups made to external hard drives, thumb drives, and so on would be vulnerable to infection – or could spread the infection themselves.
For more information on ransomware, including help with prevention, please go to https://www.nomoreransom.org. This site, a joint project of Kaspersky and Intel Security, has a great deal of information and help for those affected by ransomware. Some other helps:
Cloud backups
A cloud backup which maintains multiple versions of backed-up files allows for protection against ransomware by making it easy to revert to an earlier version. Here are some options for cloud backup.
OneDrive – allows restoration of earlier versions of Microsoft Office files. It is unclear whether or not OneDrive will maintain multiple versions of non-Office files. https://support.office.com/en-us/article/Restore-a-previous-version-of-a-document-in-OneDrive-for-Business-159cad6d-d76e-4981-88ef-de6e96c93893 has instructions.
CrashPlan – allows user configuration of multiple versions and retention settings. Different backup sets are possible (allows user to prioritize data for backup). https://www.crashplan.com/en-us/
Carbonite – keeps multiple versions of files going back up to 90 days. https://www.carbonite.com/
Security Software
Bitdefender Antivirus Plus 2017: http://www.bitdefender.com/
Kaspersky Anti-Virus (2017): http://usa.kaspersky.com/store/kaspersky-store
[1] Cisco 2016 Mid-Year Security report
[2] McAfee Labs Threat Report – September 2016
Chipped Cards: What You Need to Know
As of October 1st, retailers are supposed to be switching to card readers for EMV1 chip secured cards, moving away from the ubiquitous card swipe stations. Banks and credit card companies have been sending the new cards, which contain a computer chip as well as the standard magnetic stripe, to their consumers for some time. Now, however, if a retailer has not upgraded their credit card systems, they will be liable for any card fraud that uses a chip-equipped Discover, Mastercard or Visa card. American Express will begin holding business owners liable on October 16th.
1) Does this mean my regular card won’t work anymore?
No. The regular magnetic-stripe cards will continue to be usable for the next few years. Expect your bank and credit card providers to supply you with the new cards as they send replacements.
2) How is buying something with the new cards different from the old?
Instead of swiping your chip-equipped card, you will actually insert it into the card reader and leave it there for the duration of the transaction. This may add a little time to each transaction; retailers hope it will be small enough to not disrupt things too much.
3) What if I have a chipped card, but the store doesn’t have one of the new readers?
The new cards are all being issued with both chips and stripes, so they can be used at the older terminals. After the transition period, the stripe will be phased out.
4) Will this actually prevent credit card fraud?
It should help a great deal. The UK experienced a 63% decrease in card fraud2 – although it took three years. Until the majority of consumers are using the new cards, there are still many opportunities for criminals to continue cloning old cards. It also (currently) does not prevent online fraud. In fact, online fraud may become more common for a while. Check your credit card statements closely for the next few years3.
5) How does this work?
In a magnetic-stripe card, all of the account information needed for transactions is recorded in the strip; if someone reads that data (with a card reader, like the ones used to process payments) they can then create a copy of that card. As long as the original card remains valid, the duplicate will also be accepted. The new cards use a computer chip to generate a single-use code for each transaction. Since cloning the chip is much more difficult and would require having possession of the card for a long period of time, cloning cards becomes almost impossible. In Europe, the system also requires a PIN for purchases; while this will eventually be used here, issuers are wary of requiring too many changes at once for their users4.
1 ^EMV is an acronym derived from Europay, Mastercard & Visa
2 ^ ABC News, “What You Should Know About the New Credit Card Chip Rule” (http://abcnews.go.com/Business/credit-card-chip-rule/story?id=34148839), accessed 1 Oct 2015.
3 ^ NBC News, “Chips, Dips and Tips: 5 Potential Problems With New Credit Cards”, (http://www.nbcnews.com/business/consumer/chips-dips-tips-5-potential-problems-new-credit-cards-n436511), accessed 1 Oct 2015
4 ^ How-To Geek, “Chip Credit Cards Are Coming to the USA: Here’s What You Need to Know”, (http://www.howtogeek.com/216571/chip-credit-cards-are-coming-to-the-usa-heres-what-you-need-to-know/), accessed 1 Oct 2015.
Droning on
I am the eye in the sky
Looking at you
I can read your mind
–Alan Parsons
New technology is great. I get excited about the possibilities of how new technology can improve our lives, whether that’s our personal lives, our work lives or something else. I really love seeing innovations and technologies that allow people to do things they weren’t able to do before, or to do things more easily.
 That’s why I was so excited to attend the “4-H, Agriculture and UAVs” in-service on Tuesday – UAVs (Unmanned Aerial Vehicles) are just neat, and I was hoping there were a lot of really cool applications for them in Extension. I was ready to start buying them for my counties and helping them set them up.
That’s why I was so excited to attend the “4-H, Agriculture and UAVs” in-service on Tuesday – UAVs (Unmanned Aerial Vehicles) are just neat, and I was hoping there were a lot of really cool applications for them in Extension. I was ready to start buying them for my counties and helping them set them up.
The good news is that UAVs are as cool as I thought, even if we only got to play with some small ones. Jeff Sallee from 4-H and Dr. Jamey Jacob from MAE took us out to OSU’s Unmanned Aircraft Flight Station and let us fly some DJI Phantom 2 quadcopters. We could see how the UAVs used their attached cameras to look at things on the ground. It was amazing!
 The bad news is that there’s currently no real applications for agriculture. The FAA prohibits ALL commercial use of UAVs unless a specific exemption for such use is obtained from the agency. There ARE people who are using UAVs for ag already, true. However, they are doing so in violation of Federal regulations and are probably assuming a great deal of liability should there be an accident/incident involving one of their craft. (Here’s an example of the sorts of thing that can happen: https://www.youtube.com/watch?v=law1SsMtg_g) The FAA will issue “Cease and Desist” notifications if they become aware that someone is using a UAV for commercial purposes without the proper exemption.
The bad news is that there’s currently no real applications for agriculture. The FAA prohibits ALL commercial use of UAVs unless a specific exemption for such use is obtained from the agency. There ARE people who are using UAVs for ag already, true. However, they are doing so in violation of Federal regulations and are probably assuming a great deal of liability should there be an accident/incident involving one of their craft. (Here’s an example of the sorts of thing that can happen: https://www.youtube.com/watch?v=law1SsMtg_g) The FAA will issue “Cease and Desist” notifications if they become aware that someone is using a UAV for commercial purposes without the proper exemption.
Another issue for ag use is that FAA regulations currently prohibit flights above 400 feet AGL*. Agriculture specialists tell us that good (in the sense of useful) photos of crops requires a height of more than 1000 feet AGL. FAA regs also require constant control of UAVs in flight (that is, the craft cannot be on autopilot) which means that several operators may be required to cover a large area.
However there are issues outside government regulation. Small UAVs (like the ones we were flying) don’t have a lot of range or speed which makes it difficult to cover large areas. Dr. Brian Arnall (OSU Plant and Soil Sciences) told us that current UAVs are significantly slower than other methods to the extent that he felt them to be useless for the task, at least for the present. The example presented was crop scouting which could be accomplished with current methods in a fraction of the time it takes a UAV to perform the same task.
“For the present” are important words to keep in mind when considering UAVs. The current state, whether the technology or the regulations, is not fixed in stone. The FAA is working to define better regulations for using UAVs and appears to recognize that commercial use is inevitable. They would, however, like to have good safety regulations in place before Amazon begins making drone deliveries. The technology is improving, and companies – some located in other countries – are developing UAVs with agricultural capabilities. (Precisionag.com is a good place to look for ag UAV news.) I suspect that within the next ten years we’ll see UAVs finding legal use in ag purposes, whether crop scanning or something else.
In the meantime? One of the in-service speakers compared the state of non-government UAVs today to the state of personal computers in about 1979-1980. Most people aren’t using them, most people may not even be aware of the kind of things you can do with them, but the potential for growth is there, and as hobbyists and enthusiasts find new ways of using the technology and as manufacturers incorporate those ideas into their designs, the result will be improved use of the technologies. in the meantime, an excellent way for Extension to be involved is through 4-H. There are numerous high-school and college competitions using UAVs, many also incorporating robotics techniques for autonomous behavior. These seem like a good way to get our future UAV experts started with the technology while keeping an Extension focus.
Further Information:
http://knowbeforeyoufly.org/ – a good resource for those who want to fly drones.
http://dronelife.com/ – a one-stop shop for the newest drone news.
http://www.faa.gov/news/press_releases/news_story.cfm?newsId=18295 – The new proposed FAA rules.
http://www.regulations.gov/#!documentDetail;D=FAA-2015-0150-0017 – The open docket for the new rules.
* Above Ground Level
Facebook, Faces and Lawsuits: A Cautionary Tale
“Well we all have a face
That we hide away forever
And we take them out and show ourselves
When everyone has gone”
–Billy Joel
It appears that even if we hide our secret faces away, Facebook knows about them – and is getting sued for it. For several years now, Facebook has used a facial recognition algorithm to identify people in photos posted to the site in order to suggest tagging those it identifies.
While this certainly makes tagging posts easier (and may provide some unintended comedy when the algorithm makes a particularly off-base suggestion), it leads to some privacy concerns. Facebook does allow users to prevent others from tagging them in photos (through the privacy settings of users’ accounts), but it has not made it clear that it was gathering this type of data, nor is it clear what it does with the data, besides using it for photo-tagging.
These concerns are at the core of a lawsuit filed against Facebook by an Illinois man, Carlo Licata, who alleges that Facebook has violated Illinois law “by not informing him in writing that his biometric data was being collected or stored, or when it would be destroyed.” Mr. Licata is seeking class action status for his suit, which would allow other users (at least in Illinois) to participate.
Facebook has already discontinued the practice in Europe, stopping in 2012 after an Austrian student requested a copy of the data Facebook had on him. He discovered that Facebook was collecting information about users without their consent and that the company was retaining information he believed had been deleted.
News like this should make you realize the sheer amount of data that is generated about each of us every day based on our computer and website usage. While it is tempting to think that we are anonymous on the Internet, that’s not true: Many different entities are tracking what we do, what we look at and who our friends are. It’s good to be aware of this and to keep an eye on lawsuits such as Mr. Licata’s; the outcome may tell us even more about how our data is being used.

Choices … iPad vs. Surface Pro 3
“I know how it sounds, trust me on this
Your life to be hangs on this one choice
Keep your Hilti near, you’ll know when
Twenty minutes of oxygen”
–The Darkest of the Hillside Thickets
In the last week (although you may have missed them) a couple of significant tech anniversaries occurred. The Apple iPad, first tablet to really become popular, turned five, and Microsoft, perhaps the best-known software company ever, turned forty. Since it’s one of the perennial questions we get, I thought I’d take the opportunity to discuss the relative merits of the iPad and Microsoft’s tablet, the Surface Pro. (I haven’t really used any Android tablets, so I don’t have an opinion on them.)
First of all, it’s important to recognize that there is a significant difference in the prices of the two devices. The newest iPad, the iPad Air 2 with Retina display starts at $479, although you can spend up to $809 on one with 128 GB storage and a cell data plan. The Surface Pro 3 starts at about $800 and will generally wind up costing about $1000 – $1100 in its most useful configurations. Is the price difference justified? Basically, yes. Whether the extra cost is worth it or not will depend on what you plan to use the device to do, but a straight comparison of the two shows why the Surface costs more.
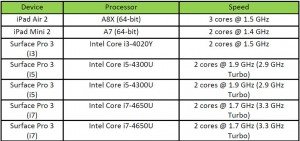
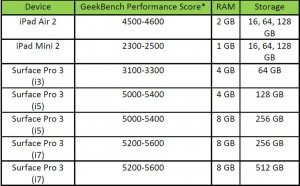
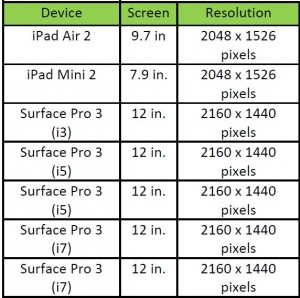
Basically, the Surface Pro has better processors, more RAM, a larger display and (generally) more storage. The extra cost is for legitimate reasons, but is it worth it? The answer is “Maybe – it depends on what you need.”
I have both an iPad Mini and a Surface Pro 3 i5, and I use both daily. What I find is that I use them for different things. The iPad is quick and easy to use – the iOS touch interface is (mostly) easy and intuitive to use. The Surface is more awkward for me to use like a tablet, even though it’s running Windows 8.1, which is definitely easier than Windows 8 was. Still, I generally set it up with its TypeCover keyboard and use it like a lightweight laptop rather than a tablet.
The iPad is quite a bit slower to switch between tasks when I’m trying to do multiple things. It’s also given to more flaky behavior in the Safari browser than Chrome or Firefox on the Surface. (The lack of browser choice on the iPad is also an issue for me – although Mozilla claims that they are working on a “Firefox experience for iOS” which will be out sometime this year. Maybe I’ll finally have bookmark synching between my iPad and my other browsers – but I’ve had that all along with the Surface. Safari on iOS is very definitely a mobile browser, and some sites just break when it tries to read them – one of my favorite blogs constantly crashes if I try to read it on the iPad. Others reload constantly, or display in odd ways.
The smaller size of the iPad Mini is sometimes nice – I can fit the device in my coat pocket or the side pockets of cargo pants. This also means I’m more likely to carry it around, and so I find I use it a lot for light internet and for email checking. The Surface, however wins easily if I need to do any serious browsing or email. For email, I’m not running an app – I’m running Outlook 2013, and the experience is just like on my desktop. I can send attachments easily and do things like look people up in the GAL. Since I’m connected directly to the Exchange server, there are never any calendar synchronization issues. Overall, mail on the iPad is great for quick checking and reading messages, but if I need to do anything else, it’s much better on the Surface.
Transferring files to or from the iPad is pretty easy with Dropbox – but the Surface also runs Dropbox, and also has a USB port so I can use a thumb drive. Taking notes that synchronize with my desktop computers is easy with the iPad and Evernote – but the Surface can run Evernote too, as well as the whole Microsoft Office suite, so I can use Word if I want to take notes, and use OneDrive to synchronize the file.
Overall, the iPad is a great tablet, but the Surface is a tablet/laptop hybrid, and it winds up being superior in almost every case where I need to do work. For just checking email and doing some very basic stuff while mobile, the iPad is great, but for really working, give me a Surface Pro. Does that mean it should be your choice? Not necessarily. You may need a particular app that only runs on the iPad, or you may only need a device for light email and internet use, in which case the smaller size of the iPad would be an important factor. I can’t tell you what to get, but I hope you’ll consider what you want to do with your device and think about which of these would work better for your needs.
*”Geekbench 3 provides three different kinds of scores:
Workload Scores: Each time a workload is executed Geekbench calculates a score based on the computer’s performance compared to the baseline performance. There are two workload scores for the same workload as Geekbench executes each workload in single-threaded mode and in multi-threaded mode.
Section Scores: A section score is the geometric mean of all the workload scores for workloads that are part of the section. These scores are useful for determining the performance of the computer in a particular area. See the section descriptions above for a summary on what each section measures.
Geekbench Score: The Geekbench score is the weighted arithmetic mean of the three section scores. The Geekbench score provides a way to quickly compare performance across different computers and different platforms without getting bogged down in details.
When comparing scores, remember that higher scores are better, and double the score indicates double the performance.” For more details, see this: http://support.primatelabs.com/kb/geekbench/interpreting-geekbench-3-scores
Superfish, Privdog and other Scary Beasts
You may have heard something about Lenovo computers and something called “Superfish”. (If you’ve actually heard of “Privdog”, you can skip the rest of this article – you’re already well ahead of the game.)
(more…)
Hello Barbie and the Internet of Things
“I hear the secrets that you keep/When you’re talking in your sleep.”
–The Romantics
Hello Barbie is Mattel’s newest Barbie doll; the company demonstrated the doll at the New York Toy Fair in February and plans to begin selling it this fall.. Mattel says that the doll was designed in response to its marketing surveys, which indicated that the thing most little girls wanted was to be able to talk to their Barbies. Hello Barbie can not only talk, she can talk about the things her owners are discussing. How? The doll has a microphone that can record speech when a button is pressed. The recording is then transmitted over Wi-Fi to the Internet, processed and analyzed, and then Barbie says something in response. This is similar to the way Siri works, but it’s the first time it’s been done to a toy.
So just to make it simple:
- This doll records conversations around it when a button is pressed.
- The recordings are sent to a company’s servers.
- Speech analysis determines what is being said.
- An appropriate response is sent back to the doll.
This is all part of the Internet of Things (IoT)”, a term you’ve probably heard recently. The idea is that the Internet, once a way of hooking together computers to share information, will now also become a way of connecting almost every item we use. This way, we’ll all have access to important information at any time, and we’ll be able to control our devices from almost anywhere. There are some real benefits to the idea. Controlling your heating/cooling system to make sure your house is at a comfortable temperature when you’re there becomes much easier and more efficient. Devices that are wearing out can report their status so you don’t get caught by unexpected failures. There also some very serious privacy concerns as well, however.
In the case of Hello Barbie, I wonder what else Mattel will do with the data generated from the recorded conversations. Will the company use it for marketing? (I’d be surprised if it doesn’t.) Who controls it – Mattel, the company’s partner or someone else? What safeguards are there to keep Hello Barbie’s data secure as it travels from the doll to the Internet and back?
ToyTalk has addressed some of these concerns, but has it done enough? I don’t know. I know what the company has said, and I know how much I trust large corporations to keep their word when there’s a strong financial incentive to break it. And even if it does do what it has said, I know how endlessly creative the hackers are and how insecure much of the infrastructure of the Internet is.
As we implement more and more of the Internet of Things, we’re going to see more security holes. We need to think about each new thing we connect to be sure it’s safe, whether it’s a television or a doll.
Free Software
“Sign upon the dotted line … nothing’s free. Eventually, nothing’s free.”
–Alice Cooper
Free software is a cool thing. It’s nice when you identify something you need to do (convert a file type, etc.) and then find a good, free tool for doing it. And, of course, a great deal of what we do with computers relies on free software, from Adobe’s PDF reader to Java, from Microsoft Security Essentials to Firefox or Chrome.
There are a couple of problems with free software, though. One is that malware profiteers know that people who are looking for free software can be tricked into downloading malware, so they create sites to take advantage of people who are Googling terms like “free Acrobat” (or other software names). Since you’re expecting to download and run an installer, all they have to do is lie about what you’re getting. One of the tip-offs that you may be getting tricked is the download link. Is it actually from the manufacturer of the software? For example, is your Acrobat download from adobe.com or adobe-pro.softonic.com? There’s a difference (see this article if you want more information), and you want to make sure you’re on the right site. I’ve seen about five different people in the last month who have infected their machines by trying to find free software; in every case, the software was something that our regular NiNite installer would have installed for them.
Another issue is that a lot of free software is now getting bundled with adware and other unwanted programs, even if you download it directly from the maker. So you download your free software and run the installer, and it installs the thing you were trying to get – and also some adware, some fake anti-malware and some system tools that only slow your computer down. Now you’ve got pop-ups and fake anti-malware giving you warnings and asking for your credit card number, and all you wanted to do was to read a PDF.
This is another thing that NiNite was designed to do: Install software without the add-ons. Some of you have probably used our NiNite installer for the free tools we use in OCES. It’s a convenient way to install or update these items. You can also build your own at Ninite.com, if the one on our site doesn’t have what you’re looking for.
If you need something that NiNite doesn’t offer, contact us; we often know about tools that may help you out. We can also check out tools that you’ve found and make sure they don’t install anything bad. Free software is something we all need to use, but it’s not worth messing up your computer.
Domain Names
“It took the night just to find the place.
A minor quirk in the navigation.
I’m so confused that I don’t know if we’re coming or going” – The Darkest of the Hillside Thickets
I ordered pizza the other night, and after about half an hour, got a call from the pizza driver. “I’m out front,” she said. I thought it was odd that she hadn’t rung the doorbell, but said, “OK, I’ll be at the door in a second,” and hung up. I then opened my door to see … no one. I waited a few seconds and then called the restaurant and explained what had happened. A minute later the driver called back. I opened the door and … still no one. I started asking questions like, “Where are you?”
“In front of your house.”
“No, I’m on my porch and I don’t see you.”
I started walking down my drive, looking up and down the street. Then I saw the car, parked in front of my neighbor’s house. I told the driver, “You’re at the wrong house.”
“Well, that’s where my GPS said to go.”
I paid for my pizza and went back inside, wondering about her future as a driver. Both my house and my neighbor’s house have numbers on them. That didn’t help her because she wasn’t looking at the numbers, just at what her GPS said.
The Internet is sometimes that way; we don’t always pay close attention to the websites we go to. Oh, we know the addresses of the ones we use all the time, but we may not always take a close look at links before we click them. Sometimes that’s just being too much in a hurry to take care, and sometimes it’s because we don’t really know what a Web address means.
Everybody knows an address begins with “www” and ends with “.com,” unless it’s “.edu” or “.org” or something else, right? Except sometimes an address doesn’t have a “www” in it. Why is that? Most people don’t know. In fact, the real addresses of the Web are IP addresses; each device (server, PC, tablet, smartphone, etc.) attached to the Internet has to have one. An IP (Internet protocol) address is a unique number to identify every device, so that your browser, email and other applications can find their way from one side of the Internet to another. The things we humans call addresses are URLs (uniform resource locators) and they’re part of the Domain Name System. The reason the system exists is that it would be incredibly difficult for us to remember the actual IP addresses (“Now let’s see, Google is 216.58.216.196, and OSU Mail is 139.78.99.99 …”); hence URLs.
The Domain Name System (DNS for short) defines how the URL looks based on a hierarchy. At the highest level are what are called top-level domains , which tell you what type of website you’re connecting to. This is the part that comes at the end of the URL: .com, .edu., .org and so on. Some of them describe what type of entity owns the address: .com for businesses, .org for non-business groups, .edu for universities, .mil for U.S. military. There are a lot of these. There are also two-letter TLDs that identify the country in which the domain is registered. You can see a full list of TLDs here: http://en.wikipedia.org/wiki/List_of_Internet_top-level_domains.
The next part of the address is the actual domain name, the part for which you have to register (and generally pay). The domain name is paired with a TLD for registration purposes, so registering “okstate.edu” is not the same as registering “okstate.com”; businesses and other organizations will often register as many of the most popular TLDs for their domain name as possible to help with branding and to avoid confusion.
The next parts of the URL are also important, although a working URL can have one, several or none of them. This is where (if it’s used) you can find the “www” in addresses; this part is intended to identify the actual server that is hosting the website or other Internet service (e.g., email). This section of the URL can be multiple names, which indicates a hierarchy of services within the domain, whether by a separate server, a virtual machine or some other method. So our support site, http://support.dasnr.okstate.edu shows that we are the DASNR support group at Oklahoma State University; the mail site, http://mail.okstate.edu is pretty obviously the mail server at OSU.
Using server names deceptively is also often a method used to trick people into thinking that they’re clicking on a good link when they’re not. If I want to scam people into giving me their bank account info, I can get more people to click my fake link if it points to something like “http://citibank.12.com” than if my URL reads “http://www.12.com.” Using a word that people expect to see in the URL makes it harder to spot the problem. It’s a good idea to scan the URLs of any links you’re planning to click pretty closely so you can spot any bogus links.